Amplifying Risk in Retail Stores
The evidence to date on the technologies that aim to make shop thieves think twice
Table of Contents:
- Abstract
- Introduction
- - Understanding the Offending Decision
- - Understanding the Shop Thief
- - Amplifying Risk
- - Methodology
- Methods of Amplifying Risk
- - EAS Tagging Technology: Research Study Results
- Video / CCTV: Research Study Results
- - Signs, Stickers and Campaigns: Research Study Results
- - Security and Sales Staff: Research Study Results
- - Store Design, Layout and Mirrors: Research Study Results
- - Shelf-based Interventions: Research Study Results
- Studying the Amplification of Risk in Retailing
- - Making Risk Amplification Visible
- - Making Risk Amplification Credible
- - Making Risk Amplification Intelligent and Proactive
- Summary of Key Findings
- Store Design, Layout and Mirrors
Languages :
The purpose of this report, which was published in 2016, is to review the available evidence on what is known to date about the efficacy of a range of methods and devices utilised by retailers to try and amplify risk in their retail stores. It is based upon an extensive review of the publicly available literature stretching back 30-40 years.
The report describes in detail the idea of ‘risk amplification’ whereby retailers can employ different ways to enhance prospective offenders’ concerns about the likelihood of apprehension. The study looks at six types of intervention: Tagging Technologies; Closed Circuit Television; Signage, Product Stickers and Campaigns; Security and Sales Staff; Store Design, Layout and Mirrors; and Shelf-based Interventions.
In terms of tagging technologies, the study found: evidence is generally positive but most studies lack rigorous and robust methodologies; all tags need to be highly visible or their presence ‘advertised’ on product packaging; hard tags seem to be more effective than soft tags; opportunistic would-be thieves are much more likely to be deterred by the presence of tagging technologies than professional thieves; and the technology struggles with a credibility issue relating to false alarms and the lack of a credible response at store exits.
With regards to CCTV: few studies have measured the direct impact of CCTV on retail store losses; results are largely inconclusive; its presence in stores make staff more confident to approach customers behaving suspiciously; and opportunistic thieves are more likely to be deterred by its presence than professional thieves.
The results for Signage, Product Stickers and Campaigns were: most studies are now very dated and employ methodologies with small samples and study periods; previous studies suggest they have an effect on levels of loss although the most recent study (2011) did not record any real impact.
With regards to Security and Sales Staff: numerous studies conclude that ‘people’ can play a very important role in amplifying risk; store guards can be effective but they need to be mobile and in close proximity to offenders; retail staff utilising good customer service practices can be very effective; both opportunistic and professional thieves regard retail store staff as an effective deterrent; staff can play an important role in reducing the anonymity of would-be thieves, a key prerequisite for some offenders when deciding to commit a crime or not.
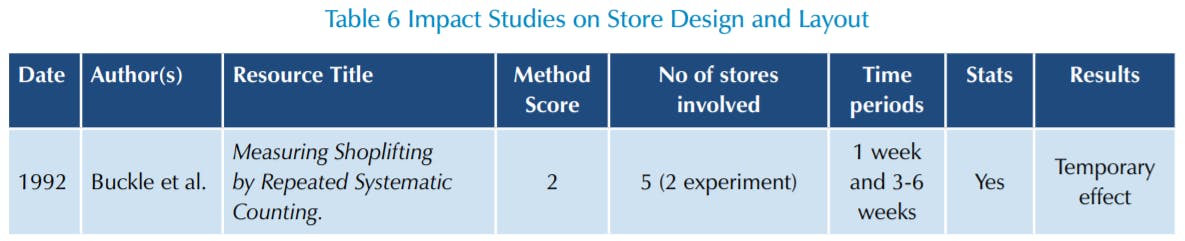
The results for Store Design, Layout and Mirrors were: good store design and layout was found to be very important in providing the context for the amplification of risk by other interventions; it is important to ensure all retail staff have good line of sight in the store, especially of high-risk products – avoiding high shelving, cluttered spaces, narrow aisles; store design and layout needs to facilitate the use of formal mechanisms of surveillance, such as CCTV and security guards; there is no evidence to suggest mirrors amplify risk and they may simply offers ways for offenders to monitor the movement of retail staff.
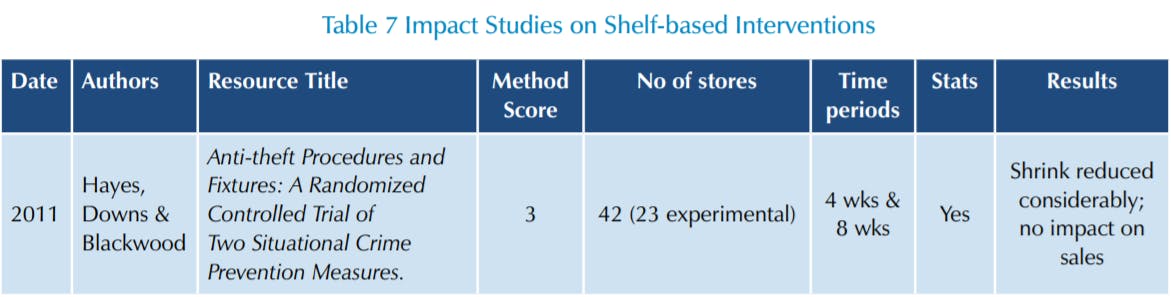
Finally, the review of shelf-based interventions concluded that: only one poorly designed study was found which showed that a device to slow down the removal of products from the shelf, together with an alert each time a product was taken reduced levels of shrinkage considerably without affecting sales.
Abstract
The purpose of this report, which was published in 2016, is to review the available evidence on what is known to date about the efficacy of a range of methods and devices utilised by retailers to try and amplify risk in their retail stores. It is based upon an extensive review of the publicly available literature stretching back 30-40 years.
The report describes in detail the idea of ‘risk amplification’ whereby retailers can employ different ways to enhance prospective offenders’ concerns about the likelihood of apprehension. The study looks at six types of intervention: Tagging Technologies; Closed Circuit Television; Signage, Product Stickers and Campaigns; Security and Sales Staff; Store Design, Layout and Mirrors; and Shelf-based Interventions.
In terms of tagging technologies, the study found: evidence is generally positive but most studies lack rigorous and robust methodologies; all tags need to be highly visible or their presence ‘advertised’ on product packaging; hard tags seem to be more effective than soft tags; opportunistic would-be thieves are much more likely to be deterred by the presence of tagging technologies than professional thieves; and the technology struggles with a credibility issue relating to false alarms and the lack of a credible response at store exits.
With regards to CCTV: few studies have measured the direct impact of CCTV on retail store losses; results are largely inconclusive; its presence in stores make staff more confident to approach customers behaving suspiciously; and opportunistic thieves are more likely to be deterred by its presence than professional thieves.
The results for Signage, Product Stickers and Campaigns were: most studies are now very dated and employ methodologies with small samples and study periods; previous studies suggest they have an effect on levels of loss although the most recent study (2011) did not record any real impact.
With regards to Security and Sales Staff: numerous studies conclude that ‘people’ can play a very important role in amplifying risk; store guards can be effective but they need to be mobile and in close proximity to offenders; retail staff utilising good customer service practices can be very effective; both opportunistic and professional thieves regard retail store staff as an effective deterrent; staff can play an important role in reducing the anonymity of would-be thieves, a key prerequisite for some offenders when deciding to commit a crime or not.
The results for Store Design, Layout and Mirrors were: good store design and layout was found to be very important in providing the context for the amplification of risk by other interventions; it is important to ensure all retail staff have good line of sight in the store, especially of high-risk products – avoiding high shelving, cluttered spaces, narrow aisles; store design and layout needs to facilitate the use of formal mechanisms of surveillance, such as CCTV and security guards; there is no evidence to suggest mirrors amplify risk and they may simply offers ways for offenders to monitor the movement of retail staff.
Finally, the review of shelf-based interventions concluded that: only one poorly designed study was found which showed that a device to slow down the removal of products from the shelf, together with an alert each time a product was taken reduced levels of shrinkage considerably without affecting sales.
Introduction
Retailers are not short on advice as to how they might manage the risk of shop theft in their physical and virtual stores – a considerable consulting and technology-based industry has developed around them offering a plethora of ways to try and achieve this goal1. It is easy to see why this has happened – the challenge is considerable and even the best ‘solutions’ often struggle to maintain their potency – the shop thief (both external and internal) can be highly adaptive, innovative and brazen in the approaches taken to relieve retailers of their produce2. This is further compounded by the almost constant change witnessed in the retail world, which has become for many an absolute necessity if they are to maintain market share and continue to generate a profit3. This almost continual cycle of change brings with it not only new opportunities to maintain and grow sales but also opportunities for theft to occur – the perennial double-edged sword – requiring those tasked with managing the problem to be equally flight of foot in how they adapt and respond.
Understanding the Offending Decision
The work of Cornish and Clarke and others has developed a body of knowledge that provides a solid framework for better understanding how offenders think and the way they go about making decisions to steal and, perhaps more importantly, the factors that can act to deter them4. This research suggests that offenders assess the following factors before coming to a decision: the perceived risk (how likely is it that I will be caught?); the relative ease with which the offence can be committed (how easy is it for me to do this?); the benefit of undertaking the offence (what will I get from doing this and is it worth it?); and the likely consequences if they were to be caught (what will happen to me if they catch me?).
If they decide that the risk is low, that it is easy to do, well worth the effort and even if they were to be caught the consequences would be low, then they are highly likely to go ahead and offend. Of these factors, it has been found that the first (the risk of being caught) is the most important in an offenders’ decision-making process, while consequential punishment is regarded as the least important5. For retailers, it is difficult to impact upon all four of these factors to the same extent and some are more susceptible to their control the others. For instance, retailers are certainly able to influence the degree to which an offender feels like they may be caught and how easy it is to carry out a crime, and while they can impact to a degree on reducing the benefit obtained (such as utilising benefit denial strategies)6, it is much more difficult to influence this factor given the nature of their business (selling goods of value)7. Equally, while retailers can try and impact the ‘punishments’ associated with crimes against their businesses (for instance pursuing approaches such as civil recovery) it is relatively difficult to influence criminal justice systems and governments to make this happen.
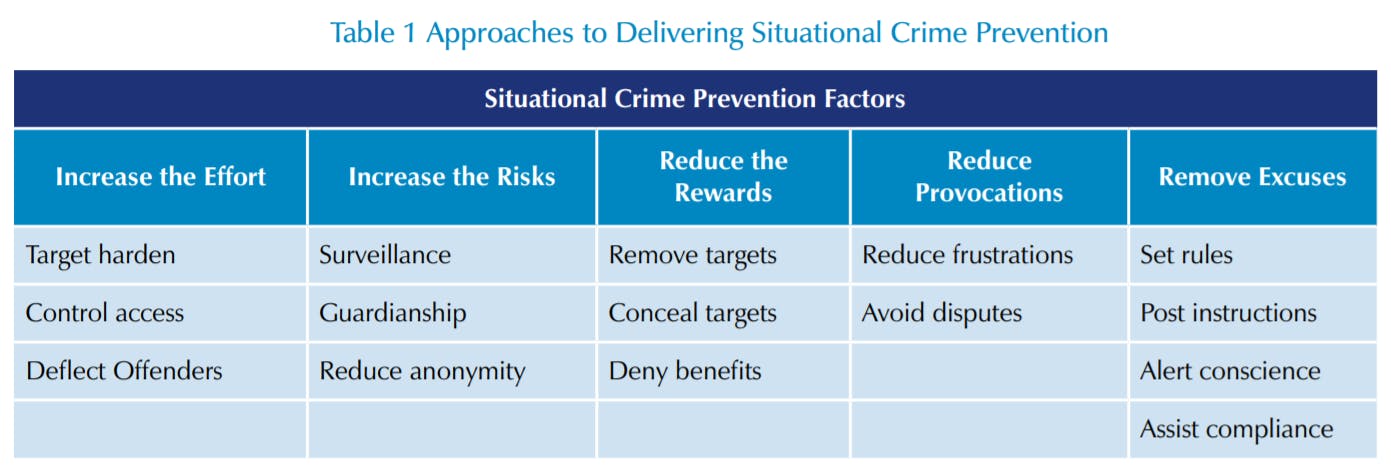
Building on this thinking has been work on how to influence these decisions, particularly through changing the situation in which the offender operates. A useful summary of this approach can be seen below in Table 18. As can been seen, a series of factors have been identified as ways to try and influence the decision-making and circumstances surrounding a prospective offender. For instance, ways have been developed to make it harder for the offender to commit a crime, such as through ‘target hardening’, limiting their access or encouraging them to go elsewhere. Similarly, and of particular interest to this report, ways have been developed to increase the risk such as by increasing surveillance and guardianship and reducing the amount of anonymity enjoyed by the offender. Likewise approaches have been developed to reduce the rewords, make it less likely that the offender will be provoked into offending and removing any possible excuses they might have to commit an offence.
Understanding the Shop Thief
Of course there is no such thing as the ‘typical’ shop thief; many typologies have been developed trying to capture the characteristics of those who come into retail stores to steal products, described rather euphemistically by some as ‘non-paying customers’ or those ‘engaged in consumer product acquisition’9! For many a key and somewhat simplistic distinction is often drawn between those who are regarded as rather opportunistic/amateur in nature, not having any real predefined plan to steal, taking product when they can, principally for personal use, and those that are regarded as ‘professional’, often working with others and mainly stealing products so that they can be converted into cash10.
Knowing what proportion of those who steal from retail stores are in each of these camps has proved almost impossible to determine, as has the proportion of losses that they are responsible for11. Some research studies have attempted to provide evidence to help better understand this profile of offending, such as the National Retail Security Survey undertaken in the US on an annual basis, which asked respondents in 2007 how many of their shop thieves did they think were amateur versus professional, with the former being considered to be vast majority (76%), but it did not capture what proportion of the value stolen might be accounted for by these two groups12. A best guess would suggest that there are far more opportunistic than professional thieves in circulation (otherwise it is highly likely most retailers would have gone bankrupt by now) but that professional thieves account for a greater value of losses per incident. Why does this matter? Well, it matters for a number of reasons, the most important of all being that research has shown that the impact of interventions designed to stop or minimise theft vary considerably in their effectiveness depending upon the type of offender that comes across them13. Well-organised professional thieves often have a very different attitude towards security interventions they come across, regarding them as something of an inconvenience to be managed, than more opportunistic thieves who are much more likely to be deterred by their presence14. Deterring and indeed detecting professional shop thieves often requires a very different approach, sometimes requiring changes in legislation (such as the moves in the US to tackle Organised Retail Crime (ORC)), highly trained and dedicated security teams, frequently working with local police forces to identify and prosecute offenders, and a considerable on-going budget15. Moreover, professionals are likely to adopt thieving strategies that can be extremely difficult for shop staff to deal with – often brazen, frequently confrontational, and highly likely to be intimidating. Getting caught is sometimes seen as ‘simply a bad day at the office’ or an inevitable but somewhat regrettable part of the ‘job’16. They are also likely to be continually developing new ways to circumvent crime prevention approaches introduced by retailers – described by Ekblom as the arms race of crime prevention17. These types of thieves present a considerable challenge to not only the retailers themselves, but also the associated security industry tasked with supporting them.
On the other hand, the more opportunistic thief is much more concerned about being caught, and while not always acutely aware of security interventions designed to make it more difficult for them to steal items, can be relatively easily deterred18. For many of these types of thieves, if the opportunity is not present to steal at that time then the offence will simply not happen – they are far less likely to seek out alternative targets. Arguably, most anti-theft interventions are explicitly designed for this type of offender – they are much more likely to be taken seriously by them and reduce the likelihood of offending19. However, in order for the opportunistic thief to be effectively deterred from taking advantage of the opportunities they perceive to steal, they must be not only aware of the security intervention but they must also believe it is credible – they must see it and they must believe it is going to increase their chances of being caught20. If it is perceived not to be credible then there is a much higher risk that an offence will take place. So, what is key to effectively deterring the would-be opportunistic thief is ensuring that they are aware of credible risk in the retail environment – particularly the risk of being caught in the act of stealing a product. Therefore, the principal aim of the retailer and their associated security/technology providers is to ensure that the risk of apprehension is sufficiently ‘amplified’ in the retail environment – have they made the potential miscreant aware that a credible risk exists in the store?
Amplifying Risk
Risk amplifiers can come in many different shapes, sizes, approaches, formats and forms of intervention – hence why a considerable industry has developed creating a whole host of ways in which to prevent theft21. For the most part they have been designed to try and deter the offender – retailers have increasingly recognised that deterrence rather than detection and prosecution is a much more cost effective and manageable means to deal with the issue of shop theft22. As one grizzled old loss prevention executive once said: ‘you cannot arrest your way out of a shrinkage problem!’23. This is particularly the case if the opportunistic model of offending is subscribed to – most people will take advantage of the opportunities presented to them and will only stop when they consider the risk of apprehension to be too high, when it is considered too difficult to undertake, where the perceived reward is too low, or when the consequence of apprehension is deemed too unacceptable. As detailed earlier, this rational choice model of understanding offending behaviour offers retailers important ways in which to disrupt the would-be offender, with elevating perceived risk and increasing the difficulty of undertaking the action being the factors that retailers can influence the most. The idea of risk amplification is particularly important to the first factor – perceived risk of apprehension – if a device or an approach in a store can ensure an elevated sense of this risk, then the offender is much less likely to commit the crime. However, for this to be successful the offender must first recognise the intervention and secondly understand how it will increase the risk of being caught.
For example, retailers have the option of attaching Electronic Article Surveillance (EAS) tags to their products, which if they are not removed or deactivated at the point of sale will trigger an alarm at the door, which in turn will (should) generate a response from a nearby capable guardian (such as a security guard or a member of the retail team) who will then check whether the person has actually purchased the product causing the alarm to trigger. Through previous experience, visual awareness, media coverage and other means, most shoppers are now aware of EAS alarms in retail stores – indeed the sound of alarm activations has increasingly become the backdrop of modern retailing24. Therefore shoppers are relatively familiar with the perceived mechanism associated with seeing an EAS tag on a product – without deactivation the tag will set off the alarm at the exit producing an elevated risk that a capable guardian will find the stolen item. For most opportunistic thieves who do not know how to defeat these types of tag the perceived risk of being caught has been sufficiently elevated to deter them from trying to steal the item – the tag has acted as a risk amplifier. However, let us imagine that the EAS tag has been put inside the product, attached in such a place on the product where it is hard to see, or designed in such a way as to be unclear it is an EAS tag (such as looking like a barcode). Then the opportunistic thief is now likely to be more confident to attempt to steal the item – the apparent absence of the risk amplifier gives them a degree of reassurance that they are not likely to be caught.
Methodology
The purpose of this report is to review the available evidence on what is known to date about the efficacy of a range of methods and devices utilised by retailers to try and amplify risk in their retail stores. Not surprisingly, manufacturers and providers of anti-theft interventions often make grandiose claims about how effective their particular technology or approach is to reducing loss but there is surprisingly little independent literature published to help the retailer make investment decisions or understand how to make the most of the devices and approaches they have chosen. Through an extensive literature review, this report will detail the main approaches adopted by retailers to try and tackle theft occurring in their stores, focussed primarily but not exclusively upon external thieves (where published literature is available on how risk amplification approaches have been tested to deal with internal theft, then this will also be included). It will seek to summarise what the published research concludes, and where available, any recommendations on best practice. The report will only utilise documents in the public domain, published in academic journals and books, practitioner magazines and reports, presentations and conference proceedings and reliable online websites and other e-resources.
This report will make use of an adapted version of the Maryland Scale of Scientific Methods to try and help assess the degree of methodological rigour utilised in the published research25, although it is recognised that this approach is not without its critics26 and other approaches have been developed27. All the studies reviewed in this report will be categorised into two types: Impact Studies and Process-based Studies. The key distinction between the two is that typically, Impact Studies aim to measure the impact of an intervention on a prescribed set of indicators, for instance, measuring the impact of an intervention on levels of shrinkage or crime in a given retail space. In this respect, Impact Studies (IS) are usually designed to try and answer the ‘did it work?’ question. In contrast, Process-based Studies (PS) are typically designed to understand the effect of interventions not related to specific target indicators and may include a range of approaches that try and understand possible changes in behaviour or organisational responses to the intervention. For example, interviews with customers about how they view the issue of shoplifting would be a PS – it is not designed to evaluate the impact of a given intervention designed to tackle shop theft, but is more interested in offering contextual information about the problem itself. Similarly, a study looking at how customers respond to false alarms generated by EAS systems would be a PS – it is not measuring the impact of EAS on levels of shrinkage but is instead offering information relating to how the system is operating. For the most part, PS often but not exclusively, rely upon a range of methods including both quantitative and qualitative approaches, while IS are exclusively quantitative in nature, utilising a range of statistical techniques and tests to try and establish causation.
Perhaps not surprisingly, IS are less frequently undertaken – they are typically more expensive to undertake and require more organisation and planning than most PS. Ideally, an assessment of a given intervention would make use of both IS and PS but this is very rarely seen, again, mainly due to cost and complexity.
In the original Maryland Scale, there were three levels used to assess the rating strength of a given IS methodology: ‘1) reliable and statistically powerful measures and correlations (including adequate sample sizes and response rates), 2) temporal ordering of the hypothesized cause and effect – so that the program “cause” comes before the crime prevention “effect”, and 3) valid comparison groups or other methods to eliminate other explanations, such as “the crime rate would have dropped anyway”’28. As the Maryland Scale was primarily designed to try and assess relatively large-scale evaluations of crime-related studies, often undertaken and subsequently reviewed by/for government and criminal justice agencies, it arguably has only limited utility for reviewing the types of interventions and studies undertaken by and for the retail community. In addition, the relatively short scale (3) and height of the first point of the scale (reliable and statistically powerful measures and correlations) also means that many studies undertaken relating to interventions in the retail space would be excluded.
It is therefore proposed to use the following five-point scale to evaluate the methodological rigour of any given IS reviewed in this report:
- No published information on research methods adopted, such as sample selection and size, or evidence of any basic statistical analysis undertaken which might enable intervention affects to be meaningfully measured and understood.
- Information about the research methods used is available and some use made of statistical tests to explore the relationship between an intervention and outcome measures, such as crime levels, rates of shrinkage, impact on sales, but no use made of control groups or before and after data.
- Comparisons drawn and observed with other groups without demonstrating comparability to the treatment/experimental group, for instance impact indicators are measured before and after an intervention but not compared with control groups.
- The study makes use of control groups to compare the results from experimental groups but does not take account of other possible confounding variables.
- Comparison between multiple units with and without the intervention, controlling for other associated factors that may account for observed changes. There is random assignment and analysis of comparable units to intervention and control groups.
While this offers some degree of a scale of ‘quality’ of the methodology employed, it is not meant to be wholly definitive in assessing any given study. For instance, a study could utilise a control group but the sample size could be very small (for instance one store), which would seriously undermine the overall validity29 and wider applicability of any reported findings. In addition to the issue of sample size, the length of the research period, the response rate, the appropriateness of the statistical analysis and the reliability and validity of the outcome measures could all influence how the quality of a methodology might be considered30. All of these factors have been taken into account when reviewing the studies included in this report and where they are considered to significantly undermine methodological rigour, then the given score has been revised down accordingly.
In terms of PS, then clearly this scale is not appropriate as they are not typically focussed upon measuring changes in target indicators chosen to assess whether an intervention has had an effect and may employ non quantitative methods, making the scale above inappropriate. Therefore, no systematic review of the methodological rigour employed by a given PS will be provided beyond describing the overall approach adopted.
As stated earlier, this study has only made use of documents freely available from public and academic libraries and reliable on-line sources. The world of retail loss and its management is notoriously shy when it comes to sharing information in the public domain31. Very few companies openly publish their loss results and even fewer make available the results from internal trials of interventions introduced to better manage their losses. In many respects, this is perfectly understandable – they are commercial profitdriven organisations that recognise that the effective control and management of retail losses can and does have a profound effect upon their profitability32. As such disclosing this information could be akin to giving away company secrets that can only undermine their ability to stay ahead of their competitors. What this means is that there are probably hundreds if not thousands of unpublished projects undertaken by retailers that cannot be included in this report because they have not been made available for sound commercial reasons. Where this is particularly evident is in the case of Electronic Article Surveillance (EAS) technologies, which have been in use since the 1960s.
As will be detailed shortly, relatively few studies have appeared in the public domain, most from many years ago, all but a few with pretty poor methodology scores, offering up a rather mixed review on the efficacy of the technology, and yet thousands of retailers around the world continue to invest in it. Either those investing in EAS are exhibiting some form of ‘pack’ mentality (everybody else is using it, so we had better use it as well) or they have come to a reasoned view (hopefully informed by reliable evidence from their own trials) that it has benefit in the control of theft from their stores. Now it may be that it is a bit of both and possibly other factors as well that are informing their decision to invest, but it seems wholly implausible that the published evidence on EAS represents the definitive word on its impact on retail losses. Having said all of that, this report can only review that which is known, but it is very important that this caveat is taking into consideration when reading this document.
Methods of Amplifying Risk
The range of interventions below have been selected based upon the existence of some existing publicly available literature, be that a IS or PS. While there are a myriad of ways in which risk can be amplified in a retail store, only those that have been the focus of some form of publicly available study have been included. This limitation means that only the following interventions have been considered:
- Tagging Technologies (particularly EAS, including Safer Cases)
- Closed Circuit Television Systems (CCTV)
- Signage, Product Stickers and Campaigns
- Security and Sales Staff
- Store Design, Layout and Mirrors
- Shelf-based Interventions
EAS Tagging Technology: Research Study Results
In his detailed and comprehensive review of the history of EAS source tagging, Bob DiLonardo, a veteran of the industry, suggests that the technology has revolutionised the retail industry, providing an effective means to deter would-be thieves in a cost effective way that enables both manufacturers and retailers to profit from increased open display of product33. In addition, the consumer benefits because retailers end up losing less and can therefore pass on this saving through lower prices. It seems a perfect scenario whereby the introduction of a particular intervention provides a win for all parties – manufacturers, consumers and the retailers. As we all know, it has not been that simple when it comes to EAS and in particular source tagging, perfectly captured by DiLonardo’s summary of the progression of the industry to date: ‘the culmination of years of oscillating momentum shifts, frenzied product development, cutthroat competition, legal battles, moral suasion, testing and retesting, apathy, and resistance’34. While part of this ‘battle’ has much to do with competing technological systems vying for dominance in the market place over many decades, it is also grounded in a distinct lack of a substantial body of verifiable and publicly available information on the actual effectiveness of the technology. In this respect it has been a much-debated technology with claims and counter claims being made by retailers, technology providers and industry consultants about whether it has indeed revolutionised the control of shop theft. Before reviewing what is known to date about the effectiveness of tagging technologies and the lessons that can be learnt from the available studies, it is worth summarising how tagging is meant to operate to control theft losses in general and specifically amplify risk in retail stores.
Amplifying Risk and Tagging Technologies
As detailed earlier, effective risk amplification requires that the potential thief needs to be made aware, through some form of intervention in the store, that there is an elevated risk of being caught if they were to try and steal an item. In respect of tagging technologies, this is achieved in three main ways:
- Through the application of a physical taggant35 of some description on the product. This can be in the form of:
-- ‘hard’ tags: typically a highly visible plastic object that is firmly secured to the product, frequently by a pin-type mechanism, which can be applied at source, in the supply chain or in the store;
-- ‘soft’ tags: typically a small paper/plastic strip or label either stuck or sown onto the product or designed into/placed within packaging, which can be applied at source, in the supply chain or in the store;
-- ‘spider wraps’: a device that wraps around a product and is designed to prevent opening of the packaging as well as its illicit removal from the store; typically applied in the store but sometimes in the supply chain;
-- ‘loop alarms’: various forms of cables/ connectors attached to and through products designed to limit product movement (frequently used on tester products and certain types of clothing); typically applied in the store only and designed to trigger an alarm if tampered with;
-- ‘keeper/safer boxes’: plastic cases which typically enclose a single item and usually (but not always) have some type of taggant embedded within them; most frequently applied in the store but some companies do this in their supply chains;
-- ‘bottle tags’: a variant of the hard tag but designed specifically to attach to most types of bottles (used mainly on alcohol-based products); typically applied in the store but some companies attach them in the supply chain; and
-- ‘dye’ tags: a variant of the hard tag designed mainly for the clothing sector which contains a indelible dye that is released on to the product if the tag is forcefully removed; usually applied in-store and may or may not have alarm activation functionality. - Through the use of notices in the store and on products with taggants attached (or claiming a taggant is attached).
- Through the use of taggant reader ‘gates’ positioned at store entrances and exits that can generate an alarm (audio and visual) if a non-deactivated taggant is identified in its vicinity
The key idea underpinning the use of tagging technologies is that the would-be thief must believe that there is a real and credible risk that if they were to try and remove a product from the store without paying for it, the tagging technology attached to it will alert a capable guardian (security or sales staff), through the sounding of an alarm as they exit the store, which in turn will lead to their apprehension. While the effective delivery of this type of intervention in busy retail stores requires many elements to be in place to ensure it is regarded as a ‘real’ and ‘credible’ risk, some of which will be discussed below, in terms of this report, the key element is that the potential miscreant must ‘know’ that the retailer is using this technology in their stores. While there may be some risk awareness diffusion from experiences in other retail outlets where the technology is in use and staff respond well to it, the messaging needs to be clearly noticeable to have the desired deterrent effect.
EAS Tagging Technology Impact Cases
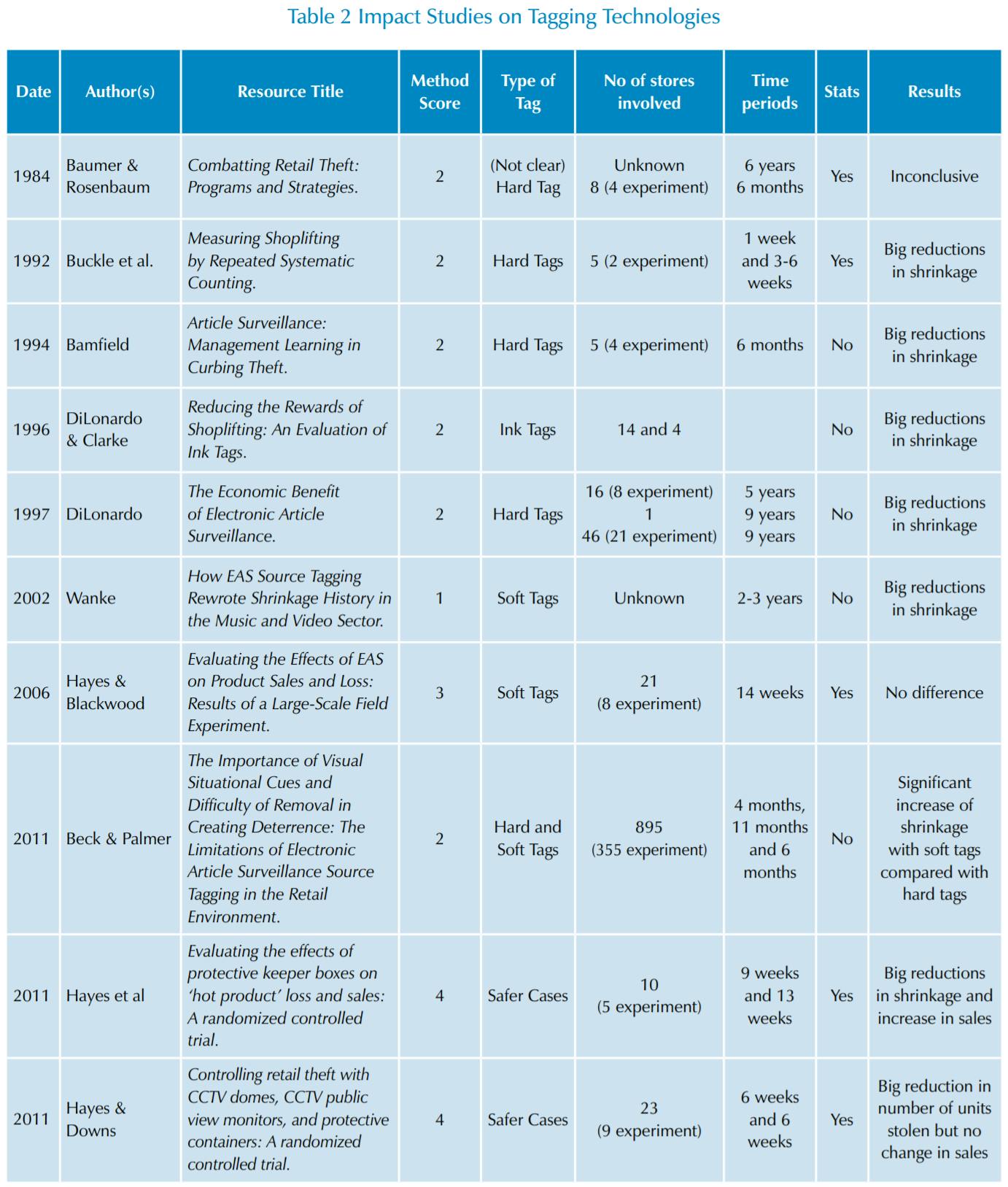
As can be seen in Table 2, 10 studies have been found in the public domain that offer some form of assessment of the role of tagging technologies – a remarkably low number for such a widely used and pervasive technology, which has been in use for over 50 years. The earliest is by Baumer and Rosenbaum in 1984, although they had reported the same findings in a report for the Westinghouse Evaluation Institute in 197936. They refer to two sets of data made available to them by retailers, dating back to 1973- 78, the first of which compared rates of shrinkage in 34 Departments (the number of stores was unknown) before and after EAS was installed. At the start the rate of shrinkage was reported as averaging 9 per cent and by the end of the five-year period it was down to 3.7 per cent. However, the authors concluded that the downward trend could not be solely apportioned to EAS and the difference was not statistically different. In the second set of data, four stores were tested against four control stores (only certain departments within each store used EAS) over a six-month period and shrinkage was found to be statistically lower in the experimental stores than in the control stores although there was no pre-test data available. The authors summarised that the data from the two studies offered mixed results with a lack of methodological rigour precluding any firm conclusions to be drawn about the role of EAS in reducing retail losses.
The second Impact Study is by Buckle et al who reported in 1992, and was based upon research looking at what impact EAS, store guards and store redesign might have on rates of shrinkage. It used an innovative methodology that required all products under consideration to be labelled with a small sticker to help signify when it had been sold, stolen or was still on open display and these were counted on a twice-daily basis. EAS was introduced in two stores and compared against three control stores. The data was collected the week before the intervention, the week after and then three to six weeks later. They recorded impressive results of reductions in shrinkage by 76% and 93%, concluding that EAS was more effective and lasting than the alternative approaches included in the study (store redesign and security guards). While this is one of the few studies to use significance tests as part of its analysis, it has been given a relatively low methodologically score because of the small sample size (just 2 stores) and the very short data collection period.
Bamfield’s study from 1994 of a single apparel retailer again has only a small number of stores involved in the trial (four stores with one control store) and returned a reduction in shrinkage of 28%, although the author admits at the beginning of the chapter that ‘the analysis is not intended to show whether EAS is, generally, effective or ineffective, but to examine how it can be used’37.
DiLonardo reported in 1996 and 1997 on trials of both hard tags and dye tags, the former based upon a summary of 30 ‘statistical’ studies but actually only utilises three cases studies, and the latter based upon two studies38. The first 1996 case study recorded a reduction in shrinkage of 17% compared with an increase in shrinkage of 30% in the non-EAS stores, although no statistical tests are reported on the validity of the findings. The second case study summarised the impact of what happened when one store had EAS installed, removed and then reinstalled, with the rate of shrinkage declining, increasing and then declining again (over a seven-year period). The final 1996 case study again looked over a very long time period (nine years) at the effect EAS had on particular departments within a store chain, comparing those with and without the technology. The results showed a 39% reduction in shrinkage after installation although again there is not mention of any statistical testing. The 1997 study summarised the findings from two case studies focussed upon the use of dye tags and found that in 14 stores using this type of tag the rate of shrinkage was 14% lower than the rest of the chain, while in a four-store trial losses after one year were 42% lower after introduction of the technology. As with his earlier study, there is no use made of statistical tests to help understand the extent to which the difference could be associated with the introduction of the tag as opposed to other factors.
These are the only publicly available pre 2000 Impact Case Studies that could be found. It is interesting to note that in other loss prevention literature, the Buckle et al, or Farrington study as it is sometimes referred to, and the DiLonardo results are some of the most quoted examples of the effectiveness of EAS technologies and yet their methodologies, certainly by today’s standards, would be regarded as remarkably weak. Since 2000, five more studies have been published, two of which utilise some of the best methodologies found in this review (both by Hayes and colleagues). Wanke reported in 2002 on his 12-year journey trying to get conformity within the music/entertainment industry on how taggants were used and applied39. In his article, Wanke refers to the ‘phenomenal’ impact the initiative had on levels of shrinkage in the pre-recorded music and video retailers, although the results are based upon returns from the various sweeps of the National Retail Security Survey rather than specific studies undertaken as part of his work. He states that in the five years since a uniform strategy of source tagging was introduced the rate of shrinkage reported by these companies dropped from 2.53% (38% higher than average) to 1.13% compared with an average of 1.75% for the rest of the retail sector. He concludes that the effectiveness of source tagging will mean the eventual elimination of the use of safer cases on these types of products.
In 2006 Hayes and Blackwood published the findings from probably the largest field study ever undertaken of an EAS technology and utilised a methodology that was considerably more robust than any previously published study on EAS40. In the context of this report, it is important to note that this study was interested in the use of tags hidden inside the products under consideration and so were not able to provide any visual risk amplifiers to the would-be thief other than through the use of alarm activation pedestals at the entrances/exits of the store. Indeed, this study was primarily interested in the impact of the pedestals rather than the tags applied to the products. The study involved using a quasi-experimental methodology across 21 stores where data was collected in control and experimental stores four weeks prior to introduction of the technology and then 10 weeks after. They used a range of statistical tests to analyse the results and concluded that source-tagged EAS did not reduce item loss, increase item on-shelf availability, or increase store-level sales in the test stores at a greater level than was found in the control stores. The study also analysed data on EAS activation activity and found that in the study period the alarm was triggered 3,732 times although no thefts were observed/identified and in just 18% of cases did a member of staff actually approach a customer who had activated the alarm.
In 2011, three Impact Cases were published – one by Beck and Palmer and the others by Hayes et al and Hayes and Downs41. The study by Beck and Palmer looked at the impact of replacing one tagging technology with another – a hard tag with a soft tag sown into the product. It was based upon one apparel retailer that operated in more than 895 stores trading under three brands across the US. In one of these brands (355 stores) in-store applied hard tags were replaced with label tags sown in at the point of manufacture (the experimental group). The remaining 540 stores continued to use hard tags and therefore acted as a control group. The results showed a considerable increase in the rate of shrinkage in the experimental stores – 251% higher than when the trial started and 53% higher than in the control group. The company decided to abandon the trial and return to using hard tags in the experimental stores and six months later the rate of shrinkage was 14% below the control group – almost identical to the starting point of the project. While the results are dramatic and seemingly underline the importance of visual deterrence, the study lacks any statistical testing of the results and therefore scores relatively poorly in terms of methodological rigour.
Hayes et al and Hayes and Down reported in 2011 on projects designed to test the efficacy and cost effectiveness of safer (keeper) boxes on sales and losses of a particular brand of razor blades. The reason why these studies have been included in this section is because safer cases very often employ a EAS tag, which can act to amplify risk. The first study (Hayes et al) was carried out across 10 stores and employed a rigorous methodology, achieving a score of four (it would have scored five were it not for the relatively small sample size). Using random assignment, five stores were selected as the experimental group, and five were chosen to be a control group with data being collected nine weeks prior to the start of the trial and 13 weeks afterwards. The study found a significant difference in rates of shrinkage – 53% lower in the experimental stores using the safer cases compared with the control group. Likewise, sales were found to have increased in the experimental stores by 69% compared with control stores. The report concluded that the investment in safer cases would return a positive return on investment (ROI) in a three-year period.
In the second study (Hayes and Downs), safer cases were again tested, using a robust methodology employing the random selection of stores as control and experimental settings (it would have received a higher score were it not for relatively small sample sizes, measurement periods and issues relating to the collection of shrink data). Safer cases were introduced into nine stores and compared against a control group of 14. Loss data was collected six weeks prior to the introduction of the safer cases and then six weeks after they had been deployed. Detailed statistical testing showed that the level of shrinkage was significantly lower in the experimental stores than in the control stores although the percentage drop is only shared as an aggregate number with other interventions being tested as part of the same study (57%).
Summary of Impact Studies on EAS Tagging
Not unlike other reviews of the literature on tagging technologies, the results are very mixed, pointing to some results that show a positive impact while others paint a less rosy picture. But there are some important points to be drawn from these studies:
- Most employ a weak methodology that makes it difficult to have strong confidence in their results. This can be seen in the small numbers of stores being used in some trials and the relatively short time periods used to collect data. Only four use any form of statistical testing.
- Most tested a hard tag of some kind (seven out of 10). Of the three looking at soft tags, two draw negative conclusions about their use.
- Taken at face value seven of the ten studies show a positive impact although when only those employing statistical tests are considered, three are positive, one is inconclusive and one shows no affect.
While the results are unsurprisingly mixed in terms of measuring the effectiveness of tagging technologies on rates of loss, not least because of the challenges of carrying out this type of project within a retail environment and implementing the technology consistently, what can be gleaned from these studies that can help understand risk amplification?42 Here the studies on the use of soft tags are particularly interesting. In terms of Wanke’s findings, the introduction of more consistent and uniform source tagging of music and video products has not seen the abandonment of other forms of protection employed to protect them as he envisioned back in the early 2000s43. Indeed, this is the category that is most likely to be seen inside safer cases in many retail outlets around the world. The application of the tag at source, sometimes within the packaging or combined with the barcode, has probably meant that the deterrent capacity of the tag has been diminished or lost – would-be thieves are not being deterred sufficiently to encourage retailers to put this type of product out on open display without the further protection offered by safer cases. This is further evidenced by the Hayes and Blackwood study and the work of Beck and Palmer, the former finding that tags hidden within high-risk products made no difference to rates of loss, while the latter found that switching from a highly visible hard tag to a far more discrete and largely invisible label tag caused losses to increase dramatically. What seems clear is that in order for EAS to work on the product itself, it must be highly visible and clearly marked for what it is – a warning to the would-be thief that attempting to steal this product will increase their chances of being caught by a member of staff.
Tagging Technology: Process Studies
Unlike Impact Studies, which are typically designed to try and measure the effectiveness of an intervention, Process Studies are usually more interested in understanding the context of the intervention or indeed a series of interventions as part of studies covering broader themes44. For instance, there have been very many studies looking at the issue of shop theft that often include questions concerning issues of retail crime prevention, which include references to tagging technologies. As such, the number of potential studies that could have been included in this review is considerable. It is therefore instructive to look at just a selection to help understand how tagging technologies might impact upon risk amplification in the retail store from the perspective of offenders and shoppers.
The research shows that professional or active thieves have only a small degree of concern about EAS tags, believe that they can readily circumvent or defeat them and do not believe that store staff will respond effectively to alarms. Various studies that have sought information from shoplifters have found relatively low levels of confidence in the deterrent impact of EAS – Weaver and Carroll reported that just 30 per cent of experienced shoplifters regarded EAS as a concern to them, Gill et al in various studies with professional thieves have found similar levels of disdain for the technology – EAS was ranked fifth out of eight possible interventions and 55 per cent said they were never deterred by it45. Hayes also reported similar results, just 2 per cent of 1,358 apprehended shoplifters indicated they would be, or are, deterred by EAS46. Slightly more positively, Lasky, Fisher and Jacques’ study of mainly self-confessed student shoplifters found that they were somewhat put off by the presence of a tag, often being displaced to steal non-tagged items, although a number of their respondents did go on describe ways in which they would defeat the tags or simply work on the presumption that staff would not respond to the alarm effectively47. It would seem that for the professional thief, EAS systems are not a significant deterrent although they do sometimes make them think about how they will go about their offending and play some part in their store selection48.
The research on the opportunistic offender is much more promising and suggests that they are much more likely to be deterred by this technology, if they are aware of its presence on the product or in the store49. They are certainly more likely to believe it is effective and are less willing to risk stealing a product where it has been utilised50. Of course, this is premised on their belief that the technology is an effective way of catching them if they were to try and remove the product from the store without paying for it – the intervention must have credibility51. This credibility can be undermined if the system is not seen to be working properly, in particular, generating a high number of false alarms. Numerous studies have looked at this issue, some of which have been mentioned earlier. A study by Handford back in 1994 found very high levels of false alarms (93%) while Hayes and Blackwood’s study from 2006 observed nearly 4,000 activations without any leading to a theft being revealed52.
The research on the opportunistic offender is much more promising and suggests that they are much more likely to be deterred by this technology, if they are aware of its presence on the product or in the store49. They are certainly more likely to believe it is effective and are less willing to risk stealing a product where it has been utilised50. Of course, this is premised on their belief that the technology is an effective way of catching them if they were to try and remove the product from the store without paying for it – the intervention must have credibility51. This credibility can be undermined if the system is not seen to be working properly, in particular, generating a high number of false alarms. Numerous studies have looked at this issue, some of which have been mentioned earlier. A study by Handford back in 1994 found very high levels of false alarms (93%) while Hayes and Blackwood’s study from 2006 observed nearly 4,000 activations without any leading to a theft being revealed52.
By their very nature, Process Studies relating to tagging technologies cover a broader range of themes than do Impact Studies – they are interested in understanding the wider context of the technology, including how offenders view them, how the technology works in practice and what if any impact they have on the shopper. The key lessons from them concerning risk amplification and tagging technologies is:
- Opportunistic would-be thieves are much more likely to be deterred by the presence of tagging technologies than those thieves that are considered to be professional.
- In order for the taggant to work successfully with opportunistic thieves it must be very clearly ‘advertised’ on the product – hidden tags or those which do not look like a security tag will not amplify perceptions of risk amongst this group.
- The system must be perceived as credible, something that can be undermined by high rates of false alarms, or taggants that are either not applied consistently across product ranges and/or are obviously easy to remove.
- While professional thieves are much more sceptical about the impact tagging technologies have upon their likely offending, they still remain wary of its use, especially when it is used in tandem with other approaches, such as proactive staff54.
Video / CCTV: Research Study Results
Like tagging technologies, the retail sector has a relatively long history of using closed circuit television (CCTV) as a means to try and control retail losses and certainly for the larger retailers then its use is almost ubiquitous. Also like tagging technologies, there is a paucity of studies evaluating its effectiveness despite significant levels of investment and its widespread use not just in retailing but across society more generally56. The late 1980s and 1990s saw its use grow considerably, especially in the UK, based upon analogue systems, spreading beyond the confines of retail stores to more public open spaces including high streets, roads, shopping malls and car parks. From the mid 2000s onwards its use has become even more ubiquitous in more countries, driven not only by developments in digital systems and significant reductions in the size and cost of the technology, but also a sense that it is now seen as an essential tool in managing risks in modern societies. It is now common place to see CCTV systems in a multitude of environments and circumstances including across most forms of public transport, ATM machines, in offices, pubs, clubs and other entertainment venues, and across networks of main roads to name but a few. Indeed, it is now almost easier to name the places where it is now not in operation – it is literally being built into the very fabric of modern societies. The consumption of this technology is also changing rapidly with traditional users such as large corporations, public authorities, such as the police, and governments being joined by individual citizens who are now equally as likely to have a CCTV system, be it in their home or indeed car. Moreover, the recording of images has moved away from something happening at fixed locations to where almost all owners of hand held computing devices now not only have the capacity and inclination to record events around them, but also the means to share those images to a global audience in real/ almost real time.. If Twenty First Century societies can be characterised as a time of rapid technological, economic and political change, they can also be seen as a time when widespread, almost saturation-like levels of surveillance have emerged.
What does all this mean in terms of the role CCTV might play in amplifying risk in the retail space? On the one hand, it could mean that would-be offenders are less likely to steal because they will expect their actions to be caught on camera – their risk will be elevated by an assumption that the ‘watcher’ will view their actions and generate a response. On the other hand, its very ubiquity could undermine its perceived effectiveness – there is so much of it that it cannot possibly be watched all of the time and therefore their actions will not be observed and they can steal with impunity.
As part of this review over 40 sources were consulted and only three could be found that would be regarded as Impact Studies in a retail setting (Table 3). The remainder are various forms of Process Studies, a number of which focus upon the retail space in particular or areas that incorporate retail spaces, such as town and city centres. These PS make use of a range of different data sources, including interviews with retail staff, customers, CCTV users, and offenders, as well as utilising data provided by various companies and more general reviews of existing literature.
Video / Closed Circuit Television Impact Cases
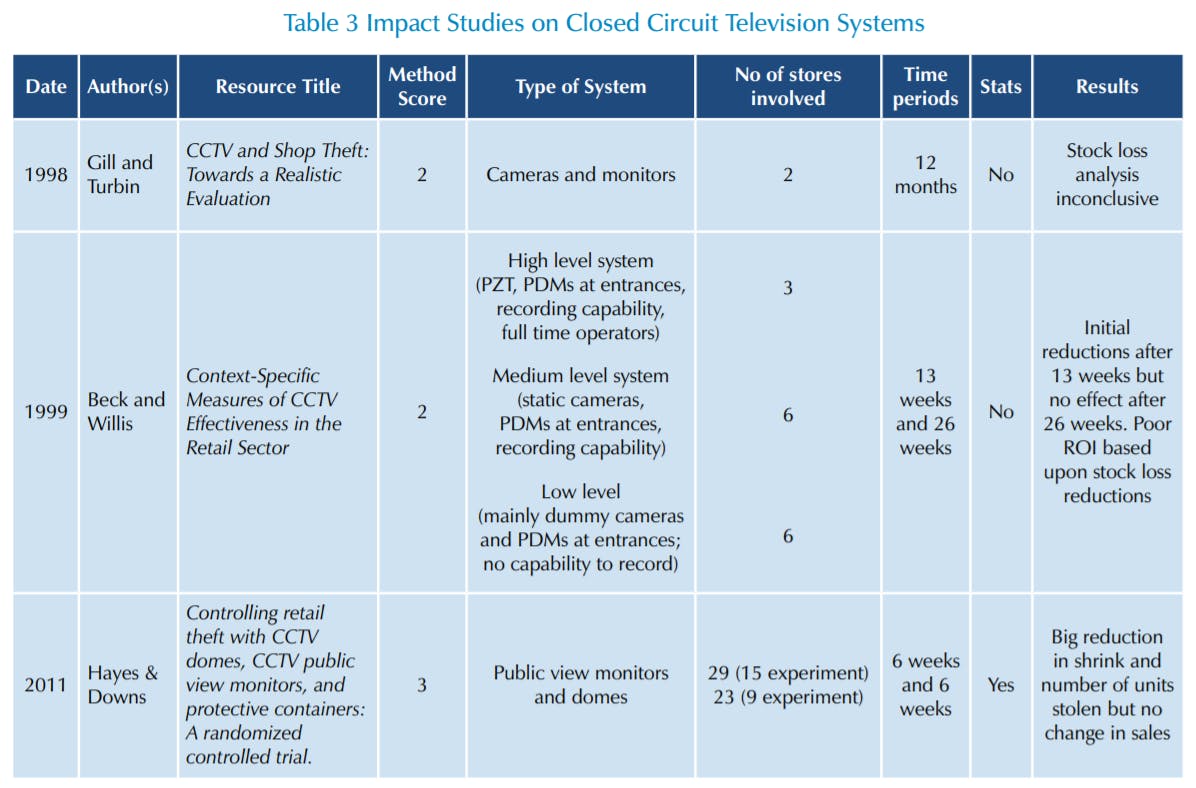
While the study by Gill and Turbin from 1998 has been included as an Impact Case study, it would be fair to say it straddles both categories, with a wide ranging methodology covering not only measurement of stock loss but also staff, customer and offender attitudes towards the use of CCTV – it is impressive for the range of data sources it used and as such offers a number of valuable lessons about the context within which this technology might operate61. The study looked at the impact of the introduction of CCTV into two apparel stores of one company over a 12-month period. The study was interested in understanding how CCTV might have an impact across a range of potential mechanisms, including staff vigilance and confidence to approach suspicious customers, identification of risky spaces within the store, increasing the perceived risk to offenders, improving the prosecution rate of offenders and reducing levels of loss. The study found that staff did feel more confident to approach customers acting suspiciously, mainly because they felt evidence was available to support them if anything should go wrong. However, no evidence was found to suggest that the rate of shrinkage was impacted by its introduction, nor was there data to conclude that more convictions were occurring. In addition, interviews with offenders suggested that most were not overly concerned about the presence of CCTV in the stores and indeed, just 1 in 5 customers stated they saw any security in the stores taking part in the trial. The study concluded that it is better to not try and ascertain whether CCTV works but more to understand how it might work in a given context.
In the following year, Beck and Willis reported on a study that aimed to measure the impact of different types of CCTV system on levels of loss, including its performance over time, and to assess whether its costs were more than compensated for by crime control benefits62. The project was carried out in 15 stores of a large UK fashion retailer with over 180 branches nation-wide. All the stores were located in similar retailing environments. Three different types of CCTV system were installed, each with varying degrees of sophistication. Three stores had a high-level system with between two and four pan, tilt and zoom colour cameras, between eight and 12 static colour cameras, public monitors positioned at all customer entrances, the facility to record and security staff monitoring the system at all times. Six stores had a medium-level system with between six and 12 static colour cameras, public monitors at each customer entrance, the facility to record but monitoring was carried out by the store manager from his or her office when time permitted.
The remaining six stores had a low-level system with up to 12 dummy cameras, public monitors at all entrances but no facility to record.
Rates of shrinkage were collected from stock takes undertaken prior to installation of the systems, after 13 weeks and then again after 26 weeks. The results proved to be mixed with stores showing an improvement in losses after the first 13 weeks, but these had evaporated after 26 weeks. The authors concluded that while offenders may have initially been concerned by the presence of the technology, its affect soon wore off – perhaps a case of over familiarity eventually breeding contempt.
The third IS was undertaken by Hayes and Downs in 2011 and utilised the most rigorous methodology found relating to any of the studies on CCTV63. It was concerned with evaluating the introduction of two different forms of CCTV technology – Public View Monitors (PVMs) and Dome cameras, both installed in the aisle where a particular hot product (Gillette razor blades) was being audited. PVMs were installed in 15 stores, Domes in 9 stores and a further 14 stores were used as control sites, all of which were allocated on a random basis. Data was collected six weeks prior and post installation and the study also tested the use of Safer Cases as part of the same project, which was reviewed earlier in this report. It was concluded that the rate of shrinkage was significantly lower in the experimental stores than in the control sites – 27% lower for stores using Domes and 57% lower for those using PVMs. The study does, however, note that the data period is relatively short and it encountered significant problems getting reliable audit data on the number of items being lost – positive shrink was identified which was then set to zero scores. This could have had the effect of over inflating the loss rate because the positive shrink numbers could have been discounted from the negative shrink numbers although given this practice was done in both experimental and control stores the overall effect would be less.
Closed Circuit Television Process Studies
A range of themes relating to the use of CCTV have been the subject of Process Studies over the past 20-30 years, including how offenders view the technology, how retail staff and customers react to it, ways in which operators of CCTV use the systems and how the technology might be used in different ways and settings. It is worth quickly reviewing what is known to date although only some relate directly to the amplification of risk. In terms of how offenders perceive the technology, then there seems to be two key findings of note. First, what might be regarded as more opportunistic thieves are typically more anxious about its use in retail stores and are more likely to be deterred than professional thieves64. While studies vary in the degree to which this second group take account of the use of CCTV in retails stores, a rough consensus would be that they are aware of it, and it can have an impact upon how and where they go about their offending. A term frequently used in these studies of thieves is that CCTV is something that needs to be ‘managed’ to ensure it does not lead to arrest65. The study by Lasky et al found that their sample of relatively active, mainly student shoplifters tended to take this view – the technology made them more careful in how they went about their offending, trying to ensure they did not conceal goods directly insight of a camera, but on the whole they took the view that it was unlikely the systems were being monitored in real time and so posed relatively little risk66.
A number of studies have sought information from retailers themselves about how they perceive CCTV and its impact upon crime and loss in their companies. Some have concluded that it can be a doubleedged sword, leading to retail staff thinking they no longer need to play a role in store security, others have highlighted its use but regard it as not being as effective as other interventions such as EAS and attentive staff67. Equally a considerable number of studies have focussed upon the views and use of CCTV systems by camera operators, noting the different ways in which they interact with the technology and how they go about deciding whom to focus their attention on when surveying customers68. Many studies have undertaken reviews of existing literature or data made available by retail and non-retail users to draw their conclusions. These have included looking at how to use CCTV to monitor consumer behaviours and marketing, creating safer retail environments, the remote monitoring of locations, managing issues of privacy, tracking consumers and measuring footfall and how various CCTV stakeholders share information69. A meta-analysis undertaken in 2009 of 41 evaluations of CCTV interventions from around the world found that its use had a very modest but overall positive impact on reducing crime70. Of particular interest to the issue of risk amplification are those studies that have sought the views of members of the public about CCTV. Typically these have found low levels of concern about use of the technology, relatively low levels of awareness of its actual use, the importance of signage and the messaging used, and how the public’s awareness can fade over time if their attention is not re-stimulated71.
It is therefore a very mixed picture when it comes to understanding the role of CCTV in amplifying risk in the retail environment. Perhaps the most important data comes from those studies focusing upon the views of offenders. Here the message seems clear, opportunistic offenders that are aware of its presence are likely to be deterred to some degree while professional thieves are likely to look for ways to defeat it.
Signs, Stickers and Campaigns: Research Study Results
Another approach employed by retailers to amplify risk is to use various types of signs, stickers and media campaigns aimed at drawing the attention of the would-be thief to either the risks and consequences of being caught or the use of particular types of loss prevention technology within the store environment. As an approach, signs have a long track record within retailing and while most existing Impact Studies are now rather dated, a number of attempts have been made to try and measure their effect on retail losses. The use of signs/advertising has also been seen in other crime prevention settings, where it has been seen to play an important role as part of an initiative72 but also that it must be seen as credible for it to have any effect, particularly in the retail sector73. In addition, the field of behavioural science has looked at the way in which signs incorporating images of watching eyes can have an effect upon the likelihood for people to behave in more socially desirable ways and have a positive impact on levels of offending although as yet this has not been tested in a retail environment74.
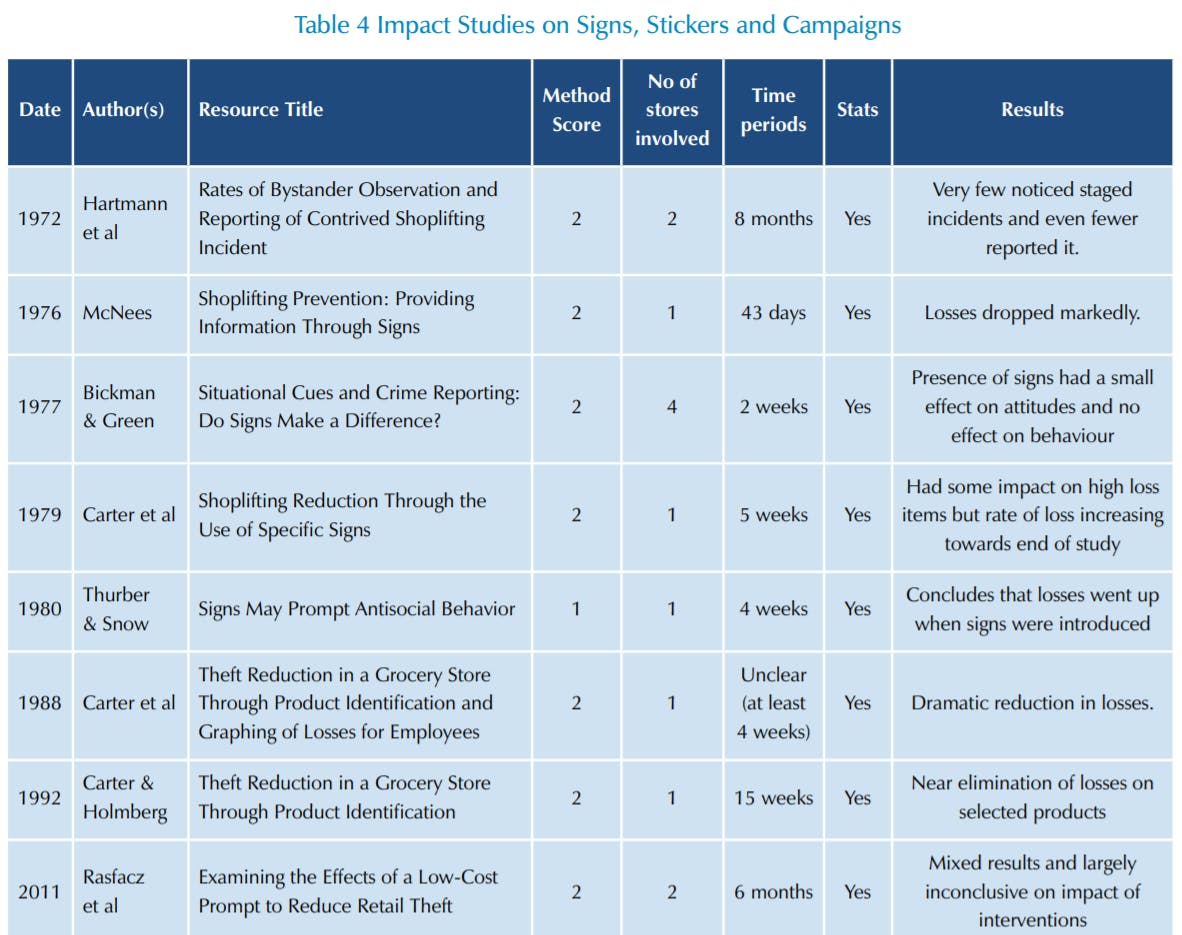
This review has focussed upon eight studies dating back to 1972, with the most recent being undertaken in 2011 (Table 4).
The first by Hartmann et al looked at whether customers would be aware of notices and incidents of shop theft, and whether they would report them to store staff75. It found that few customers ever really noticed a shoplifting event (despite the researchers making them quite obvious) and those that did typically were disinclined to report to a member of staff (most were concerned about the consequences of getting it wrong). More promisingly, a study undertaken in 1976 looked at the use of signs around a store notifying customers that shoplifting was a crime as well as putting notices near, and stickers on, at risk products76. It was only carried out in one Department store and measurement was based upon daily audits of particular at-risk products over a 20-day period. It found that losses dropped markedly from 1.3 items per day to 0.88. For those items where a sticker was attached notifying the public this was a high theft item, losses went from 0.66 per day down to 0.06. The study recorded no obvious displacement of theft to nearby items.
In the following year, Bickman and Green carried out a study similar to the Hartmann et al study in 1972 and found that the presence of signage made no difference to the likelihood of shoppers to report staged incidents of shoplifting77.
The fourth study undertaken in 1979 in Sweden by Carter et al attempted to replicate the study done by McNees et al in 197678. It was carried out in just one store over a five-week period and focussed upon preidentified high risk products from different parts of the store: lip gloss, leather coats, Elvis Presley records and halogen bulbs. The study utilised the methodology of systematic counting using stickers, as seen in the later Buckle et al study on EAS, store guards and store redesign79. After set periods of time the signs were placed in the vicinity of the target products stating: ‘Attention! Customers! The items marked with a red circle are frequently stolen by shoplifters’. The results showed that losses on lip gloss were reduced from 18% to 9% (statistically significant), on Elvis Presley records from 9% to 3% (not statistically significant), on leather coats from 18% to 0% (statistically significant), and on halogen bulbs from 31% to 10% (statistically significant).
The following year (1980) Thurber and Snow undertook a similar study in one US store looking at cigarettes80. In a ludicrously short study they measured losses for one week and then put up a sign for one week saying: ‘Cigarettes are the items most often shoplifted’, the following week replaced it with a sign saying: ‘Everyone pays for shoplifting’ and then the following week took the sign away. The ‘results’ showed that losses went from 3% to 5% to 4% and then back to 3% in this four-week period. They argued that the signs acted as evoking stimuli, encouraging people to steal the cigarettes.
Carter and colleagues have completed two further studies of interest, one in 1988 and the other in 1992. The former was focussed upon employee theft and looked at how by making staff aware of the products most likely to be stolen, losses would be reduced81. They found that through regular updates (twice a week) losses of monitored products dropped from an average of 8 per day to 2 per day, the reason being, they argued, was that staff thought these items were under careful management scrutiny and therefore increased the risk of being caught trying to steal them. The latter study in 1992, again undertaken in just one Swedish store, once again tested the use of signs and making customers aware of high theft items82. Data was collected for 38 weeks prior to the start and then after 5 weeks and 10 weeks. High-risk theft items were identified from a series of store audits (mainly health and beauty products such as shampoo, toothbrushes and sanitary napkins). These items were clustered in one aisle of the store and at the start of the experiment two signs were hung at each end of the aisle stating: ‘Customers – items marked with a red circle are frequently stolen by shoplifters!’. In addition, a red circle was placed on the shelf edge next to the at risk items. Results showed a statistically significant reduction in losses on these items, from an average of 3.71 items per week to 0.19 per week.
The final and most recent study dates from 2011 and was undertaken by Rafacz et al83. They set out to repeat the studies undertaken by Carter and colleagues in the 1970s, 80s and 90s to see if the use of signs and shelfedge ribbons would reduce levels of loss. Undertaken over a 6-month period in two stores, 23 high loss items were allocated to different experimental processes (signs and shelf edge ribbons, only signs, and no signs or ribbons). Unlike most of the earlier studies, the results were largely inconclusive in terms of trying to gauge the impact on sales and losses – they concluded that signs and shelf-edge ribbons made little difference.
Few other studies have been found looking at the impact of signage on retail loss although some have included a question about signs as part of broader studies looking at how offenders in particular view various forms of security interventions84.
As can be seen, most of the studies on signs, stickers and awareness campaigns are now really very old indeed, undertaken when retailing was a very different experience for both the consumer and the retailer. It is instructive looking at some of the experimental results how high the levels of loss were on some items although in many respects the types of items deemed vulnerable to loss remain largely unchanged. All of the studies suffer from major methodological weaknesses, particularly in terms of the low numbers of stores used, the lack of control stores and the very short measurement periods – some as little as a week. As we know, shrinkage numbers are incredibly volatile, and particularly when starting with very high losses, a natural regression to the mean has to play a part, as does other confounding factors such as the often intense scrutiny test products were placed under as part of the research process (reducing the likelihood of staff theft in particular).
Perhaps one of the biggest difficulties in utilising loss prevention-related signage in modern retail stores is the degree to which it is increasingly lost within a landscape of advertising and product messaging/ promotional materials that now envelop the modern retail store. If as has been found in other settings, the crime prevention publicity must be credible and visible, then the retail store presents a real challenge to the loss prevention practitioner trying to raise awareness of the potential risks of apprehension present within the store. Retail stores are crowded ‘noisy’ places full of competing messaging and the likelihood is that relatively low key messaging such as those used in the studies above may struggle to be heard these days.
Security and Sales Staff: Research Study Results
While much of the focus of attention within the world of retail loss prevention seems to be on the use of a broad range of technologies to try and address a myriad of threats, it is easy to forget the potential role people can play in amplifying risk in the retail store. This can take the form of formal security guardians such as guards and security officers, as well as the role played by store associates themselves. As detailed at the start of this report, theoretically, the role of a Guardian in influencing the decision-making of offenders is key – they can act as a powerful disincentive to offending and therefore play a very important role in amplifying risk in the retail store.
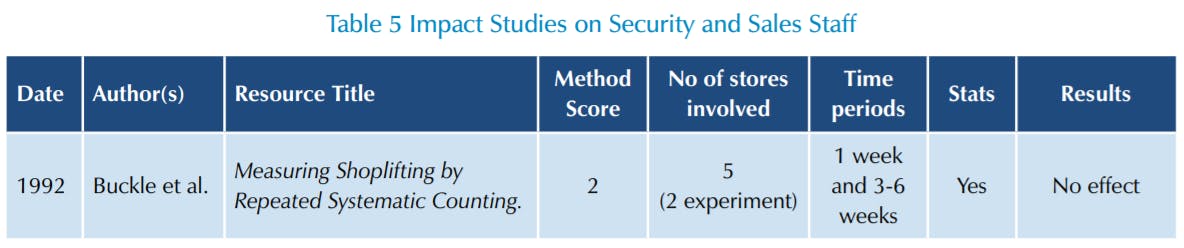
Given this, it is interesting that this review has found just one Impact Study designed explicitly to test the role of people in controlling shrinkage and other retail losses, although there are a considerable number of Process Studies which have looked more generally at the role of people in helping to manage and control losses (Table 5)85.
In 1992 Buckle et al undertook a study to compare the effect of three different types of intervention: EAS, store guards and store redesign on levels of retail loss. As detailed earlier, this study is one of the most cited in terms of the potential impact EAS can have on retail losses but it also offered interesting results in terms of the other interventions tested as part of the study. As noted earlier, methodologically, it is weak, with few stores, and very short recording periods, making the results open to criticism. What it found in terms of store guards, which were introduced into two highrisk stores, with shrinkage results measured the week before, and then three and six weeks after deployment, and compared with a control group of three stores, was that they had no effect on levels of loss in the research time period. It should be noted that a subsequent review of this study by one of the original authors notes that the guards were of poor quality – one had never been a guard before the experiment and repeatedly asked store staff what they should be doing, while the second guard was described as ‘aged 60 and relatively small and therefore unlikely to deter shoplifters’86.
While no other Impact Studies are available to counter or confirm this finding, there are a significant number of Process Studies that offer a range of results that tend to suggest that ‘people’ can play an important role in amplifying risk in the retail store. The richest vein of evidence comes from a number of studies that have sought the views of shoplifters on the measures most likely to deter them from stealing.
Back in the late 1970s the potential of store staff to impact upon shoplifting was being noted – Walsh highlighted in his study of offenders how store staff had high value in frustrating shoplifters but only if they were made fully aware of their role and what to look for within the store87. In their interviews with offenders in 1985 Weaver and Carroll drew a similar conclusion although added further detail by noting how novice shop thieves were much more likely to be put off by the presence of store staff than more professional thieves (they too were concerned about them but not as much), a finding which was also found in a replication study undertaken by Carmel Gilfilen in 201388. In his interviews and role-plays with previous shoplifters, Butler found that the presence of store staff near to the target area proved a big deterrent as did security guards, but only if they actually followed the prospective offender89. Both Gill and Hayes have undertaken a number of studies with offenders and have drawn similar conclusions about the value store staff can bring in terms of deterring would-be offenders. Gill’s 2007 study provided an international perspective, bringing together the views of offenders from around the globe – Spanish and Canadian thieves in particular viewed guards as a real threat, much more so than CCTV, and something that would drive them away from offending in guard-protected stores, preferring alternative sites where there would be less ‘hassle’90. Hayes’ work concurred and added that while store guards can be effective, offenders suggested that this was particularly the case if they moved around the store rather than remaining static in one place91.
Studies have also drawn favourable comparisons between the use of people and other approaches to deter shop thieves; Guffey and colleagues reflected upon the value store guards can bring and how highly they were rated by thieves compared with other approaches adopted by retailers92. In a similar vein, Kallis suggests that human interventions may be better than electronic-based approaches at impeding shoplifters93, a view also shared by Schlueter et al94, and Kajalo and Lindblom95 whose study of store managers highlighted the role of staff in particularly dealing with vandalism, public order disturbances and as well as shoplifting. Tonglet’s study of shoppers’ views agrees, with unformed guards being considered as effective as EAS and CCTV, while those who had admitted to recently shoplifting regarded them as the most effective, stating that humans are difficult to bypass compared with technologies96. This is a view not only shared by offenders and customers, but also by store staff as well. In their 1994 study of 98 store managers, Lin et al found that they regarded customer service as the main deterrent to shoplifters97, while Langton and Hollinger found evidence to support the use of capable guardians in the store, especially where staff turnover was lower and there were fewer part time staff98. In a 2007 study of a wide range of retail data points, Howell and Proudlove drew similar conclusions and noted that the proximity of staff to customers may be a more effective inhibitor of shrinkage than many traditional formal security precautions, such as CCTV and store detectives99.
Taken together, the overwhelming consensus from the literature is that the role of a ‘guardian’ can be key in amplifying risk in retail stores, be that by a formal security-oriented member of staff, such as a uniformed security guard, or by general store staff. The evidence from interviews with offenders, particularly but not exclusively opportunistic thieves, is that being viewed or having their anonymity compromised while they are thinking about or in the process of undertaking a dishonest act, works well in reducing the likelihood that they will continue to try and steal from a retail store. In addition, the research suggests that retail staff themselves view this as an important and effective way of generating deterrence, perhaps more so than other more technology-based approaches. But, it is dependent upon store staff recognising and understanding the role they can play and for store guards in particular, understanding the importance of not being static in the store and engaging with customers who may be acting suspiciously. As quoted by many studies, the old adage that the best line of defence against shop thieves is good customer service would seem to hold true. Within the boundaries of this study, risk would seem to be best amplified by knowledgeable, alert and customer-focussed employees engaging with those that are acting suspiciously.
Store Design, Layout and Mirrors: Research Study Results
The penultimate area for consideration is the role that store design, layout and mirrors can play in amplifying risk in the retail store. The nature of the retail store is changing quickly with increased competition from online retailers in particular, causing more traditional bricks and mortar companies to consider how they use their physical spaces now and in the future100. The way in which the design of buildings and spaces can have an impact on offending has a long track record101, particularly in urban settings where it is known as Crime Prevention Through Environmental Design (CPTED): ‘CPTED is an environment-behaviour theory and methodology based on the proposition that enlightened architecture and site design deters criminal behaviour and reduces fear of crime’102.
Few studies have been completed looking at the retail environment and how it might impact on the likelihood of offending to take place, and only one could be found which would be regarded as an Impact Study: the Buckle et al study from 1992, which has been discussed earlier with regard to EAS and security guards (Table 6)103.
The study also considered the role of ‘store redesign’ as a third way to reduce store shrinkage although the extent of ‘redesign’ was rather limited and appears to have been not much more than store staff moving high risk items nearer to the checkout so that they had a better view of them. The study found that initial positive differences in levels of shrinkage in the experimental stores where this ‘redesign’ took place disappeared over time but it was noted that store staff were increasingly not continuing with the policy of moving high risk items because it was affecting sales, which they were measured on, compared with levels of shrinkage, which they were not measured on104! The authors concluded that this store ‘redesign’ could offer lasting low cost benefits if staff were properly incentivised to take part.
Like the other areas considered in this report, studies have utilised the views of offenders, customers and retail staff to help understand how store design and layout may have a role to play in reducing the risk of shrinkage. In terms of offenders, Carmel-Gilfilen interviewed novice and expert thieves to understand how they viewed a number of factors when considering the decision to offend, including the design of the store105. She found that offenders were particularly concerned about the extent to which the store layout enabled (or not) their miscreant behaviour to be noticed through informal and formal surveillance, the latter being via CCTV systems. Factors which could influence this were the extent to which the positioning and height of shelves limited sight lines for staff at checkouts, and the amount of ‘clutter’ and crowding in the store, as one of her interviews said: ‘I wouldn’t even try shoplifting here, because it’s so much space. It’s so open, this would make me afraid to take anything’106. Carmel-Gilfilen’s work concludes that not only can the store layout influence the decision not to offend, it can also have an impact upon the likelihood to offend as well – bad design can create blind spots and opportunities that expert offenders in particular will actively seek out. She believes that there needs to be symmetry between the use of security devices/ technologies and the design of retail stores – with the former easily being undermined by the latter.
Gill’s study of offenders from around the world also highlighted the important role of surveillance and the need for retail staff to have good lines of sight within the store, particularly of high risk products107. Canadian offenders in particular mentioned the deterrent capacity of wide-open spaces in retail stores. Cardone’s 2006 work with offenders generated similar conclusions and highlighted four areas in particular: the importance of natural surveillance, extended guardianship, formal surveillance and target hardening as ways to reduce retail losses108. Crowe agrees and offers three types of surveillance as being influenced by design: natural (where all users of a space have the ability to see what is happening); organised (where staff have the ability to look out for offending); and mechanical (where devices extend the ability to detect offending)109. In a similar vein, Lawrence suggests that retail offenders are most concerned about the extent to which a store layout creates the opportunity for them to be seen, suggesting they will ask themselves three questions in this respect: Can I be seen, if I am seen will I be noticed, and if I am seen and noticed, is anybody going to do anything about it?110. This is further reinforced by Kajalo and Lindblom’s interviews with retail store managers in Finland who highlight how important ‘formal’ and ‘informal’ modes of surveillance are to controlling crime and how they can be influenced by store layout111.
It is worth mentioning at this point the use of mirrors in the store environment, as they have been a measure used for a very long time – as early as the 19th Century – and often built into the fabric of stores112. The idea is simple – enable store staff to monitor areas not directly in their line of sight and make potential offenders aware that they can be seen even when away from areas directly surveilled by members of staff. To date no systematic assessment has been undertaken on this crime prevention approach and researchers are divided on whether they are an effective countermeasure or actually compromise store security. Some have argued that it can help staff to monitor both customers and staff113 while others have suggested they are counterproductive, enabling shoplifters to use them to keep a covert watch on store staff when they are attempting to conceal merchandise114. Until further research is undertaken, it is not possible at this stage to offer any concrete evidence on whether mirrors are effective at controlling retail crime or amplifying risk115.
Clarke offers a number of practical factors that need to be taken into consideration when thinking about how store design may influence offending, which are:
- Enable staff to exercise surveillance.
- Reduce the number of exits, blind corners, and recesses.
- Carefully place mirrors.
- Provide good, even lighting.
- Eliminate clutter and obstructions.
- Place (high risk) goods away from entrances and exits.
- Create clear sight lines in aisles and reduce the height of displays.
- Reduce crowding near displays of high-risk items.
- Move hot products into higher-security zones with more staff surveillance.
- Speed up checkout to reduce congestion and waiting, which provide the opportunity for concealment116.
Finally and returning to the excellent work undertaken by Carmel-Gilfilen in this area, she offers a comprehensive summary of five key elements of how retailers need to think about store design and layout and how it can help to reduce losses and in some circumstances amplify risk:
Natural access control: Limits entry into a facility or space through built and natural obstacles. Examples include locks, cables, cases and security guards.
Natural surveillance: Enhances the capability of the occupant and observers in a facility to see what is happening around them without special action. Examples include the placement of employees, products and physical features, aisles with long lines of sight and monitoring systems like CCTV.
Natural territorial reinforcement: Establishes territories within a store to create a sense of ownership over the area. This increases the vigilance of users, by sending the message that trespassers will be identified. Examples include countertops, flooring, ceiling and lighting designations.
Maintenance: Incorporates strategies to keep spaces looking well cared for and crime-free. Maintaining elements such as lighting, paint, signage and aisles communicates to customers that management is responsible for upkeep.
Legitimate activity support: Promotes allowing users to engage in activities supported by the space by encouraging them to make claim to the space117.
Shelf-based Interventions: Research Study Results
The final area for consideration in this report is the use of interventions designed to try and amplify risk at the shelf, either through the design of the shelf itself, or the fixture/display mechanism for the product. Here the availability of studies is very low indeed – just one study could be found which has undertaken any form of test in this area (Table 7).
This study was undertaken in 2011 by Hayes and colleagues and focussed upon the use of two interventions designed to try and control the loss of razor blades in one pharmaceutical company in the US118. The Impact Study employed a rigorous methodology, utilising a randomised controlled trial in 42 stores over an eight-week period. The intervention of interest here was a protective on shelf fixture that required the consumer to press a button, which generated an alert tone and opened a small window for them to access the product. The idea behind this was that it would slow down the theft of multiple items and make the would-be offender feel more at risk of being caught (because the alert tone would draw attention to them). The intervention was introduced into 23 stores and was compared against a control group of 19 stores. Data on sales and shrink were measured four weeks prior to its introduction and then eight weeks after. As with another similar study undertaken by Hayes and colleagues119 they faced difficulties in collecting reliable audit data and decided to zero out any data where there were ‘positive’ shrink numbers (where more stock was in the store than inventory records suggested there should). While understandable, this could cause significant issues concerning the data where shrinkage was negative – the positive shrinkage numbers may have been as a consequence of poor counting of these numbers. In addition, the authors also recognise the shortcomings relating to the short study period and the use of only one retailer, but it still represents, compared to the many other studies reviewed as part of this report, as a rigorous study applying many very good methodological processes.
The study found that there was a statistically significant difference between the rates of shrinkage in control and experimental stores – 56% lower in the latter, while no difference was found in the overall rate of sales between the two groups. While these numbers are impressive, there was no review of Return on Investment (ROI) for this intervention and so it is unclear how cost effective the measure might be.
Studying the Amplification of Risk in Retailing
This final section of the report will endeavour to draw some conclusions from this extensive review of the existing literature on ways in which interventions may play a role in amplifying risk in retail store. Firstly, it is worth reflecting on the conclusions that can be drawn about the range and types of studies that have been found focusing on retail-related interventions before going on to consider the overall conclusions that can be drawn from the research.
This review has shown that there is a significant paucity of high quality published evidence on what interventions work and why when it comes to managing shrinkage and other forms of loss in retailing. Much of the evidence is really quite old, in many cases dating back 20 and 30 years, making it difficult to equate the findings to the very different context which retailing now finds itself. Moreover, societal changes in terms of how consumers now think about the retail space and interact within this environment have undoubtedly seen a quantum shift in the last two decades or more. Equally, it is highly likely that the motivations and methods of prospective offenders have changed as well – it is questionable whether the profiles of offenders and their reasoning for offending have remained completely static, although some replication studies have found remarkably similar results120. In addition, innovations and developments in retailing, such as self-scan checkouts and on line shopping, present research environments never envisaged when these original studies were undertaken.
It is also clear from the review of the available Impact Studies across the range of interventions considered in this report that most have relatively weak methodologies, with a significant number undertaken in the 70s, 80 and 90s that would struggle to be published in academic peer-reviewed journals today. Of particular concern for the vast majority of the Impact Studies reviewed is the relatively short data collection periods used, sometime as little as one or two weeks. As is well known, retailing is an enormously dynamic environment, where things can and do change quickly – drawing conclusions from short time periods within these environments is unlikely to be representative of what is likely to happen in the longer term. This is particularly the case where an intervention has been carefully monitored and controlled by researchers and retail staff for the short lifetime of the project in ways that are simply unsustainable in the real retail world. The Hawthorn effect, where improvements are due to the effects of the study itself, and performance attrition, where an interventions’ effect declines over time, are rarely controlled for or properly measured in many of the Impact Studies undertaken in the retail space121.
A significant number of Impact Studies rely upon the rate of ‘shrinkage’ provided by the retailers that have agreed to take part. This is problematic data in terms of its accuracy and its frequent inability to capture in any way the component parts which make up this number122. Fortunately, data sources within retailing have improved significantly in the last 10 years and so future studies will hopefully have better access to metrics that more accurately capture the impact any given intervention may be having.
There is undoubtedly a progression towards the greater use of more sophisticated and nuanced methodologies, as seen by the work of Hayes and colleagues and this is to be welcomed. In the busy, complex and pressured world of retailing it is inherently difficult, if not impossible to try and control for all possible confounding factors when evaluating the impact of a given intervention – researchers need to adopt approaches which utilise good practices but face up to the reality that undertaking studies that would meet the standards seen when researchers are for instance, testing drugs in the medical world, are highly unrealistic.
There are far more published Process-focussed Studies than Impact Studies – perhaps not surprising given the difficulty and complexity involved in developing and managing the latter. There is much to be learnt from the former, particularly concerning the views of offenders, customer and retail staff. As Tilley and others have argued, the question is not always strictly ‘what’ works but more often about understanding ‘why’ something does or does not work in a given context123.
For retailers this is important but it should also not be forgotten that in the cutthroat business world, the bottom line is the bottom line and investment-grade decisions need to be based upon good evidence that a return will be forthcoming, particularly when the Loss Prevention function is likely to be in competition with other retail functions also bidding for increasingly scarce investments funds. How that return is measured is typically but not exclusively going to be financial – in some circumstances the ‘value’ of a given intervention may be much more intangible and hard to quantify and yet can still add value to the business. A good example of this is CCTV, which many studies show rarely generates an explicit ROI in financial terms, but can add value in many other ways, some being far harder to measure than others, but are still deemed important to a retail business (such as staff and customer reassurance). It is in this context that many of the Process Studies reviewed in this report can add value – they provide lessons on how interventions can have a positive impact beyond the simple notions of sales and recorded losses. They also enable retailers to better understand how interventions need to be managed in their particular environment – very often the failure of an intervention to impact upon losses is more about how it is being used rather than an inherent flaw in the intervention itself.
As detailed at the start of this report, it is only possible to review that which is published and publicly available and there is no doubt that many retailers and suppliers around the world have undertaken their own studies to ascertain the ‘value’ associated with any given intervention and how it can best be managed, and these results have remained unpublished for sound commercial reasons. Undoubtedly retailing is an increasingly important, if not pivotal part of the economies of many countries around the world, and arguably they have an increasingly moral and ethical imperative to play a role in ensuring societies are as free as possible from the problems that crime can bring124. In this respect, it is important that they endeavour to try and share as much information as possible (in ways that are not detrimental to their commercial well-being), through involvement in future projects and sharing their experiences through bodies such as the ECR Community and the Retail Leaders Industry Association (RILA)125.
The Amplification of Risk
Risk Amplification, as detailed earlier, it is but one part of the jigsaw that is required to be put together to control losses in retail stores. Making would-be offenders feel that there is an elevated risk of being caught is an important piece of the jigsaw as has been demonstrated through this review of the existing literature. It is worth, therefore trying to summarise what the key elements in an effective Risk Amplification strategy might look like based upon this review.
Making Risk Amplification Visible
What seems clear from all the available evidence is that interventions must be highly visible if they are to play a role in amplifying risk – there is no point in hiding it away or making it less than obvious to the would-be thief – modern retail loss prevention should be focussed upon deterrence not detection. For interventions such as EAS, this means making the presence of the product taggant abundantly clear – hiding it away inside the packaging does not represent a good use of the technology, especially if its presence is not indicated on the packaging. The available studies that found that EAS reduced levels of loss were mainly those that had utilised a hard tag, with one report finding that where a hard tag had been replaced with a less visible paper tag, retail losses increased dramatically126. It needs to be very obvious to the would-be thief that a product is protected, and where taggants are concerned, it needs to be either very visible and obvious what it is or its presence needs to be very clearly marketed on the product packaging. How this ‘marketing’ might be achieved has begun to attract some preliminary research but more needs to be done.127
Equally, the exit/entrance gates need to be clearly visible and recognisable for what they are – part of a system designed to raise the risk of being caught. Here the growing use of gate advertising ‘shrouds’ as a means to generate additional revenue for the retailer is interesting. Does this use impact upon their visibility to the would-be thief – are they blurring the message by in some way masking their primary role? Further research could explore this issue.
This also has broader concerns relating to the use of RFID technologies in general and the increasing desire to build the monitoring technology into the fabric of the store in particular. The original and much waited-upon RFID revolution, whereby all products will be tagged with an embedded tiny grain-of-sand size taggant, their presence recognised by ubiquitous readers, enabling the Internet of Things to be realised, is unlikely to happen with the current technologies available128. But it does raise issues about how this type of approach fits with the need to make would-be offenders feel at risk through being visibly aware that a risk of detection is present. It could be that this is achieved through overt messaging and marketing of the technology within the store, although the most recent studies on this suggest this impact may be limited, not least due to the increasingly ‘noisy’ spaces retail shops have become129. More research is required on the emerging range of sensing technologies now being introduced into the retail space and how they can be utilised to amplify risk.
Generating visibility, particularly for some interventions such as CCTV, may prove increasingly challenging – their growing ubiquitous presence may undermine their ability to amplify risk in the retail environment, although research on Public Display Monitors (PVMs) suggest that it can be achieved with a degree of success, in the short term at least130. More research is required on how new forms of CCTV technologies, such as PVMs may help to amplify risk, particularly at self checkouts, where opportunities for deviant behaviour would seem plentiful together with plausible and defendable excuses for the wily thief131. It could be that new insights offered by behavioural sciences could be utilised with this type of technology to impact upon perceptions of risk as well as notions of honesty132.
Where the evidence from this review has been very consistent, if lacking the depth of analysis offered by Impact Studies, is the role people can play in amplifying risk. It would seem that both retail sales staff and dedicated security employees are regarded by opportunistic and more determined professional thieves alike as a key deterrent. But staff must be visible and very often proximal to the offender to be successful in amplifying risk – they need good lines of sight and in respect of security guards, they need to be mobile, moving around the store. Currently, many retailers employ security guards at the entrances/exits of stores, frequently ‘watching’ CCTV and (hopefully) responding to EAS alarms. The evidence would suggest that guards are unlikely to observe thieves on CCTV in the act of concealing goods in the store (unless they have been provided information from others about a suspicious customer), that professional thieves in particular are not put off by the presence of CCTV in the store, and guards are unlikely to apprehend people through EAS alarm activations (only a small percentage of alarms generate a check of a receipt). Given this, it would seem useful to understand more how security guards can be better utilised in the retail space, both as ‘risk amplifiers’ and ‘safety reassurers’, and how they can better employ the technologies made available to them such as CCTV.
For retail staff, the research suggests that they need to be made fully aware of their importance in amplifying risk and how they can deliver this effectively. It would seem that the attributes that make an employee good at being a retailer, particularly being highly customerfocussed, are also those that seem to generate the highest rates of amplified risk in the would-be offender. For most retailers their biggest expense line is paying for the people they employ – it would seem sensible to ensure that this ‘investment’ is utilised fully to not only sell more but also ensure customers steal less.
Reducing the degree of anonymity would-be thieves perceive they have is also important in the risk amplification process – something that can be achieved not only by attentive staff and alert security personnel, but also by smart technologies as well. The growing use of mobile scan and pay technologies in particular, is bringing this into stark relief, as existing risk amplifiers are made redundant by this type of consumer experience133. More research is required to understand how mobile technologies might be used to amplify risk through communication with the consumer as they move through the retail store.
Making Risk Amplification Credible
While risk amplifiers need to be visible to the wouldbe thief, they also need to be credible – they need to believe that the risk of apprehension is real. Here the research from offenders and consumers, undertaken mainly through Process Studies, is particularly helpful. The research on offenders draw clear distinctions between those regarded as more opportunistic thieves compared with those that are more organised and professional in the way they go about their thieving. The former are more likely to believe that a range of interventions are effective in making it more likely they will be caught while the latter tend to view them with a higher degree of scepticism and disregard. This is particularly the case with EAS where concerns about false alarms and a lack of a credible response have plagued the industry since it was first introduced over 40 years ago. The current evidence would suggest that this is certainly taken into account by the more determined professional thief, who will develop ways to exploit this credibility gap, but less so by the more opportunistic offender, who remains easily intimidated by its presence within the retail environment. As new technologies emerge, such as mobile scan and pay, it will be important to monitor this situation to ensure that EAS’s rather battered but still potentially potent amplification capacity remains viable.
Making Risk Amplification Intelligent and Proactive
The retail space is changing rapidly, with new technologies quickly becoming integrated, such as consumer-owned mobile devices, together with greater complexity and agility being introduced across the supply chain, through developments such as online and click and collect134. This emerging retail landscape presents significant challenges to how retail losses will be managed in the future – the where, the how and the who are all likely to become more complex and diverse. But it also presents potential opportunities as well in terms of how risk might be amplified in the future, not least through the use of these very same technologies and developments. As detailed above, anonymity is often an important prerequisite for an offender to decide to commit an offence – they do not feel like they have been noticed and so their sense of risk is reduced. What new intelligence-focussed technologies might be able to achieve is more of a loss of this sense of anonymity – the store, the shopping trolley, the shelf, the product, the checkout, the car park, could all begin to be part of a person-focussed communication process with the consumer, making them aware that their ‘presence’ in the store is known. Much of this is already possible and consumers are becoming increasingly familiar with, and arguably desensitised to, the collection of their data and the potential benefits of their location being known. Future research is required to better understand how this might play out in the retail store and how risk might be best amplified through these developments. Will wouldbe thieves be less likely to steal because their identity and location is known – will the fact that they are leaving an ‘electronic trail’ behind them, which might be associated with a deviant act, be a sufficient risk to deter them?
The Risk Amplification Landscape
For retailers the existing evidence base on ‘what works’ and ‘why’ in terms of amplifying risk is complicated and largely mixed – some things seem to work, others less so – and all interventions are clouded by the context within which they are used. There is little doubt that amplifying risk in the retail store is a very important component part of reducing the threat of crime, with success hinging on the capacity of interventions to be visible and credible – both of which are intrinsically linked to delivering an effective shopping experience for the consumer.
Summary of Key Findings
EAS Tagging Technologies
- Evidence is generally positive about the use of tagging technologies but most studies lack rigorous and robust methodologies.
- All tags need to be highly visible or their presence ‘advertised’ on product packaging.
- Hard tags seem to be more effective at amplifying risk than soft tags.
- Opportunistic would-be thieves are much more likely to be deterred by the presence of tagging technologies than those thieves that are considered to be professional.
- While professional thieves are much more sceptical about the impact tagging technologies have upon their likely offending, they still remain wary of its use, especially when it is used in tandem with other approaches, such as proactive staff.
- The technology struggles with a credibility issue relating to false alarms and the lack of a credible response at store exits. Professional thieves are likely to exploit these weaknesses but opportunistic thieves less so.
- Few customers are concerned about the use of this technology in retail stores, beyond the embarrassment factor if they falsely set off the alarm.
Video / Closed Circuit Television Systems (CCTV)
- Few studies have measured the direct impact of CCTV on retail store losses.
- Results are largely inconclusive although most recent study suggests Public View Monitors and Dome cameras were associated with lower losses (short study period and so not clear whether reduction would be sustainable).
- Its presence in stores make staff more confident to approach customers behaving suspiciously.
- In terms of reducing store losses the effect of the introduction of CCTV may only last a short period of time.
- Opportunistic thieves are more likely to be deterred by its presence than professional thieves, who will typically try to find ways to ‘work’ around it.
- A large-scale meta-analysis suggests that CCTV has only a modest impact on crime (global studies covering all types of CCTV usage).
Signage, Product Stickers and Campaigns
- Most studies are now very dated – over 25 years old and employ methodologies with relatively small store samples and study periods.
- Previous studies suggest they have an effect on levels of loss although the most recent study (2011) did not record any real impact.
- Evidence from other research settings suggest that they may have an impact, especially when they utilise ideas from Behavioural Sciences, although problems of displacement may occur.
Security and Sales Staff
- Numerous studies conclude that ‘people’ can play a very important role in amplifying risk.
- Store guards can be effective but they need to be mobile and in close proximity to offenders.
- Retail staff utilising good customer service practices can be very effective amplifiers of risk, but they need to be made aware of their role.
- Both opportunistic and professional thieves regard retail store staff as an effective deterrent, often more so than a wide range of technology-focussed interventions.
- Staff can play an important role in reducing the anonymity of would-be thieves, a key prerequisite for some offenders when deciding to commit a crime or not.
Store Design, Layout and Mirrors
- Good store design and layout was found to be very important in providing the context for the amplification of risk by other interventions. Equally, poor design can also facilitate offending (providing blind spots).
- It is important to ensure all retail staff have good line of sight in the store, especially of high-risk products – avoiding high shelving, cluttered spaces, narrow aisles.
- Store design and layout needs to facilitate the use of formal mechanisms of surveillance, such as CCTV and security guards.
- There is no evidence to suggest mirrors amplify risk and they may simply offers ways for offenders to monitor the movement of retail staff.
Shelf-based Interventions
- Only one study found which showed that a device to slow down the removal of products from the shelf, together with an alert each time a product was taken reduced levels of shrinkage considerably without affecting sales. Study suffered from relatively short study period and therefore unclear whether results were sustainable over a longer period of time.
Bibliography
Ariely, D. (2012) The (Honest) Truth About Dishonesty. New York: Harper Collins.
Ballantyne, H., Medway, D. and Jones, P. (2001) ‘CCTV and Town Centre Regeneration’, Town and Country Planning
Bamfield, J. (1994) ‘Article Surveillance: Management Learning in Curbing Theft’, in Gill, M. (ed.) Crime at Work: Studies in Security and Crime Prevention. Leicester: Perpetuity Press, pp. 156-174.
Bamfield, J. (2012) Shopping and Crime. Basingstoke: Palgrave Macmillan.
Barua, A., Mani, D. & Whinston, A.B. (n.d.) Assessing the Financial Impacts of RFID Technologies on the Retail and Healthcare Sectors, Center for Research in Electronic Commerce, Austin.
Baumer, T.L. and Rosenbaum, D.P. (1984) Combatting Retail Theft: Programs and Strategies. Stoneham: Butterworth Publishers.
Beck, A. (2009) New Loss Prevention: Redefining Shrinkage Management. Basingstoke: Palgrave MacMillan.
Beck, A. (2011) ‘Self-scan checkouts and retail loss: Understanding the risk and minimising the threat’, Security Journal, 24(3), pp. 199-217.
Beck, A. & Willis, A. (1992) An Evaluation of Store Security and Closed Circuit Television, University of Leicester, Centre for the Study of Public Order, Leicester
Beck, A. (2008) Preventing Retail Shrinkage: Measuring the ‘Value’ of CCTV, EAS and Data Mining Tools, ECR Europe, Brussels.
Beck, A. and Hopkins, M. (2015) Developments in Retail Mobile Scanning Technologies: Understanding the Potential Impact on Shrinkage & Loss Prevention, Leicester: University of Leicester
Beck, A. and Hopkins, M. (forthcoming) ‘Scan and rob! Convenience shopping, crime opportunity and corporate social responsibility in a mobile world’, Security Journal.
Beck, A. and Palmer, W. (2011) ‘The Importance of Visual Situational Cues and Difficulty of Removal in Creating Deterrence: The Limitations of Electronic Article Surveillance Source Tagging in the Retail Environment’, Journal of Applied Security Research, 6(1), pp. 110-123.
Beck, A. and Willis, A. (1994) An Evaluation of Security Hardware: The Customer Perspective, Centre for the Study of Public Order: Leicester.
Beck, A. and Willis, A. (1995) Crime and Security: Managing the Risk to Safe Shopping. Leicester: Perpetuity Press.
Beck, A. and Willis, A. (1998) ‘Sales and Security: Striking the Balance’, in Gill, M. (ed.) Crime at Work: Increasing the Risk for Offenders. Basingstoke: Palgrave Macmillan, pp. 95-106.
Beck, A. and Willis, A. (1999) ‘Context-Specific Measures of CCTV Effectiveness in the Retail Sector’, in Painter, K. and Tilley, N. (eds.) Surveillance of Public Space: CCTV, Street Lighting and Crime Prevention New York: Criminal Justice Press, pp. 251-269.
Bickman, L. and Green, S.K. (1977) ‘Situational Cues and Crime Reporting: Do Signs Make a Difference?’, Journal of Applied Social Psychology, 7(1), pp. 1-18.
Bickman, L., Rosenbaum, D.P., Baumer, T.L., Kudel, M., Christenholz, C., Knight, S. & Perkowitz, W. (1979) National Evaluation Program: Phase I Assessment of Shoplifting and Employee Theft Programs – Final Report: Programs and Strategies. Westinghouse Evaluation Institute, Evanston.
Butler, G. (1994) ‘Shoplifters Views on Security: Lessons for Crime Prevention’, in Gill, M. (ed.) Crime at Work: Studies in Security and Crime Prevention. Leicester: Perpetuity Press, pp. 56-72.
Caime, G. and Ghone, G. (1996) S(h)elf Help Guide: The Smart Lifters Handbook. Toronto: TriX Publishing.
Cameron, M.O. (1964) The Booster and the Snitch. New York: Free Press of Glencoe, Collier Macmillan.
Capgemini & The Consumer Goods Forum (2015) Rethinking the Value Chain: New Realities in Collaborative Business. Capgemini and The Consumer Goods Forum.
Cardone, C. (2006) Opportunity makes the thief: An analysis of the physical cues that influence shoplifter perceptions of the retail interior and the decision to steal. MA. University of Florida. Available at: http://ufdc.ufl.edu/UFE0015826/00001/ (Accessed: 20/3/16).
Cardone, C. and Hayes, R. (2012) ‘Shoplifter Perceptions of Store Environments: An Analysis of how Physical Cues in the Retail Interior Shape Shoplifter Behavior’, Journal of Applied Security Research, 7(1), pp. 22-58.
Carmel-Gilfilen, C. (2011) ‘Advancing Retail Security Design: Uncovering Shoplifter Perceptions of the Physical Environment’, Journal of Interior Design, 36(2), pp. 21-38.
Carmel-Gilfilen, C. (2013) ‘Bridging security and good design: Understanding perceptions of expert and novice shoplifters’, Security Journal, 26(1), pp. 80- 105.
Carter, N. and Holmberg, B. (1992) ‘Theft Reduction in a Grocery Store Through Product Identification’, Journal of Organizational Behavior Management, 13(1), pp. 129-135.
Carter, N., Hansson, L., Holmberg, B. and Melin, L. (1979) ‘Shoplifting Reduction Through the Use of Specific Signs’, Journal of Organizational Behavior Management, 2, pp. 73-84.
Carter, N., Holmstrom, A., Simpanen, M. and Melin, L. (1988) ‘Theft Reduction in a Grocery Store Through Product Identification and Graphing of Losses for Employees’, Journal of Applied Behavior Analysis, 21(4), pp. 385-389.
Clarke, R.V. (1980) ‘Situational Crime Prevention: Theory and Practice’, British Journal of Criminology, 20, pp. 136-147;
Clarke, R.V. & Petrossian, G. 2013 Shoplifting, Center for Problem-Oriented Policing, Washington.
Clinard, M. and Meier, R. (1979) Sociology of Deviant Behavior. New York: Holt, Rinehart & Winston.
Cornish, D.B. and Clarke, R.V. (1986) The Reasoning Criminal: Rational Choice Perspectives on Offending. New York: Springer-Verlag.
Cox, D., Cox, A.D. and Moschis, G.P. (1990) ‘When Consumer Behavior Goes Bad: An Investigation of Adolescent Shoplifting’, Journal of Consumer Research, 17(September), pp. 149-159.
Crowe, T. (2000) Crime Prevention Through Environmental Design. 2nd edn. Boston: Butterworth-Heinemann.
Curtis, B. (1983) Retail Security: Controlling Loss for Profit. Boston: Butterworths.
Cusson, M. (1993) ‘Situational Deterrence: Fear During the Criminal Event’, in Clarke, R.V. (ed.) Crime Prevention Studies Volume 1. Monsey: Criminal Justice Press.
Davis, R. and Pease, K. (2000) ‘Crime, Technology and the Future’, Security Journal, 13(2), pp. 59-64.
Decker, S. (2003) ‘Advertising Against Crime: The Potential Impact of Publicity in Crime Prevention’, Criminology & Public Policy, 2(3), pp. 525-530.
Demkin, J. (ed.) (2004) Security Planning and Design: A Guide for Architects and Building Design Professionals Hoboken, NJ: John Wiley & Sons.
DiLonardo, R. (1997) ‘The Economic Benefit of Electronic Article Surveillance’, in Clarke, R.V. (ed.) Situational Crime Prevention: Successful Case Studies. New York: Harrow and Heston, pp. 122- 131.
DiLonardo, R. (2014a) ‘EAS Source Tagging: 20- plus Years of Innovation, Part 1’, Loss Prevention Magazine, January-February, pp. 15-20, 22, 24.
DiLonardo, R. (2014b) ‘EAS Source Tagging: 20- plus Years of Innovation, Part 2’, Loss Prevention Magazine, March-April, pp. 39-46, 48.
DiLonardo, R. and Clarke, R.V. (1996) ‘Reducing the Rewards of Shoplifting: An Evaluation of Ink Tags’, Security Journal, 71, pp. 11-14.
Dodd, C.A., Clarke, I. and Kirkup, M. (1998) ‘Camera observations of customer behaviour in fashion retailing: methodological propositions’, International Journal of Retail & Distribution Management, 26(8), pp. 1-8.
Dubash, J. (2016) ‘Marketing and the Internet of Things: Are You Ready?’, The Marketing Journal.
Ekblom, P. (1986) The Prevention of Shop Theft: An Approach Through Crime Analysis. Crime Prevention Unit Paper No. 5, London: Home Office.
Ekblom, P. (1997) ‘Gearing up against crime: A dynamic framework to help designers keep up with the adaptive criminal in a changing world’, International Journal of Risk, Security and Crime Prevention, 2(4), pp. 249-265.
Farrell, K. and Farrera, J. (1985) Shoplifting: The AntiShoplifting Guidebook. New York: Praeger.
Farrington, D.P. (1999) ‘Measuring, Explaining and Preventing Shoplifting: A Review of British Research’, Security Journal, 12(1), pp. 9-27.
Farrington, D.P. (2003) ‘Methodological Quality Standards for Evaluation Research’, The Annals of the American Academy of Political and Social Science, 587, pp. 49-67.
Farrington, D.P. and Painter, K. (2003) ‘How to Evaluate the Impact of CCTV on Crime’, in Gill, M. (ed.) CCTV. Leicester: Perpetuity Press, pp. 67-79.
Farrington, D.P., Gottfredson, D., Sherman, L. and Welsh, B. (2002) ‘The Maryland Scientific Methods Scale’, in Sherman, L.,
Farrington, D.P., Welsh, B. and Mackay, D. (eds.) Evidence-Based Crime Prevention. 1st edn. London: Routledge, pp. 13-21.
Felson, M. (1986) ‘Linking Criminal Choices, Routine Activities, Informal Control, and Criminal Outcomes’, in Cornish, D.B. and Clarke, R.V. (eds.) The Reasoning Criminal. New York: Springer Verlag.
Gibbens, T.C.N. and Prince, J. (1962) Shoplifting. London: The Institute for the Study and Treatment of Delinquency.
Gill, M. (2007a) Shop Thieves Around the World, Perpetuity Research and Consulting International, Leicester.
Gill, M. (2007b) Shoplifters on Shop Theft: Implications for Retailers, Perpetuity Research & Consultancy International, Leicester.
Gill, M. & Spriggs, A. (2005) Assessing the Impact of CCTV, Home Office, London.
Gill, M. and Turbin, V. (1998) ‘CCTV and Shop Theft: Towards a Realistic Evaluation’, in Norris, C., Moran, J. and Armstrong, G. (eds.) Surveillance, Closed Circuit Television and Social Control. Aldershot: Ashgate, pp. 189-204.
Gill, M., Bilby, C. and Turbin, V. (1999) ‘Retail Security: Understanding What Deters Shop Thieves’, Journal of Security Administration, 22(1), pp. 29-40.
Gladwell, M. (1997) ‘See me, touch me’, The Independent Magazine, (February), pp. 9-12.
Guffey, H., Harris, J. and Laumer, J. (1979) ‘Shopper Attitudes Toward Shoplifting and Shoplifting Devices’, Journal of Retailing, 55(Fall), pp. 75-89.
Handford, M. (1994) ‘Electronic Tagging in Action: A Case Study in Retailing’, in Gill, M. (ed.) Crime at Work: Studies in Security and Crime Prevention. Leicester: Perpetuity Press, pp. 175-184.
Harris, C., Jones, P., Hillier, D. and Turner, D. (1998) ‘CCTV Surveillance Systems in Town and City Centre Management’, Property Management, 16(3), pp. 1-6.
Hartmann, D.P., Gelfand, D.M., Page, B. and Walder, P. (1972) ‘Rates of Bystander Observation and Reporting of Contrived Shoplifting Incidents’, Criminology, 10(3), pp. 247-267.
Hayes, R. (1999) ‘Shop Theft: An Analysis of Shoplifter Perceptions and Situational Factors’, Security Journal, 12(2), pp. 7-18.
Hayes, R. (2012) ‘You Can Steal it, But You Can’t Use It: Moving Toward Benefit-Denial Technology’, LPPortal.com, September-October, pp. 39-46.
Hayes, R. (ed.) (2006) Shoplifting Mach 3: Offender Interviews Research. Presentation Slides. Unpublished.
Hayes, R. 2008 Lessons Learned: Shoplifter Interview Results, Loss Prevention Research Council, Florida.
Hayes, R. and Blackwood, R. (2006) ‘Evaluating the Effects of EAS on Product Sales and Loss: Results of a Large-Scale Field Experiment’, Security Journal, 19(4), pp. 262-276.
Hayes, R. and Cardone, C. (2006) ‘Shoptheft’, in Gill, M. (ed.) The Handbook of Security. Basingstoke: Palgrave Macmillan, pp. 302-327.
Hayes, R. and Downs, D. (2011) ‘Controlling retail theft with CCTV domes, CCTV public view monitors, and protective containers: A randomized controlled trial’, Security Journal, 24(3), pp. 237-250.
Hayes, R., Downs, D. and Blackwood, R. (2011) ‘Antitheft Procedures and Fixtures: A Randomized Controlled Trial of Two Situational Crime Prevention Measures’, Journal of Experimental Criminology, 8(1), pp. 1-15.
Hayes, R., Johns, T., Scicchitano, M., Downs, D. and Pietrawska, B. (2011) ‘Evaluating the effects of protective keeper boxes on ‘hot product’ loss and sales: A randomized controlled trial’, Security Journal, 24(4), pp. 357-369.
Hesse, L. (2002) ‘The Transition from Video Motion Detection to Intelligent Scene Discrimination and Target Tracking in Automated Video Surveillance Systems’, Security Journal, 15(2), pp. 69-78.
Hollinger, R.C. and Adams, A. (2008) 2007 National Retail Security Survey: Final Report. Gainsville, FL: University of Florida.
Hope, T. (2005) ‘Pretend It Doesn’t Work: The ‘AntiSocial’ Bias In The Maryland Scientific Methods Scale’, European Journal on Criminal Policy and Research, 11(3), pp. 275-296.
Howell, S.D. and Proudlove, N.C. (2007) ‘A statistical investigation of inventory shrinkage in a large retail chain’, The International Review of Retail, Distribution and Consumer Research, 17(2), pp. 101-120.
Jeffery, C.R. (1977) Crime Prevention Through Environmental Design. 2nd Edition edn. Beverly Hills: Sage.
Johns, T. and Scicchitano, M. (2006) ‘Research by Retailers: Understanding Loss and the Effectiveness of Loss Prevention Strategies’, Security Journal, 19(4), pp. 216-227.
Johnson, S. and Bowers, K. (2003) ‘Opportunity is in the Eye of the Beholder: The Role of Publicity in Crime Prevention’, Criminology & Public Policy, 2(3), pp. 497-524.
Kajalo, S. and Lindblom, A. (2010a) ‘How retail entrepreneurs perceive the link between surveillance, feeling of security, and competitiveness of the retail store? A structural model approach’, Journal of Retailing and Consumer Services, 17(4), pp. 300-305.
Kajalo, S. and Lindblom, A. (2010b) ‘Surveillance investments in store environment and sense of security’, Facilities, 28(9/10), pp. 465-474.
Kajalo, S. and Lindblom, A. (2011a) ‘An empirical analysis of retail entrepreneurs’ approaches to prevent shoplifting’, Security Journal, 24(4), pp. 269-282.
Kajalo, S. and Lindblom, A. (2011b) ‘Effectiveness of formal and informal surveillance in reducing crime at grocery stores’, Journal of Small Business and Enterprise Development, 18(1), pp. 157-169.
Kallis, M.J. and Vanier, D.J. (1985) ‘Consumer Shoplifting: Orientations and Deterrents’, Journal of Criminal Justice, 13(5), pp. 459-473.
Keval, H. and Sasse, M.A. (2008; 2010) ‘“Not the Usual Suspects”: A study of factors reducing the effectiveness of CCTV’, Security Journal, 23(2), pp. 134-154.
Kirkup, M. (1999) ‘Electronic footfall monitoring: experiences among UK clothing multiples’, International Journal of Retail and Distribution Management, 27(4), pp. 166-73.
Kirkup, M. and Carrigan, M. (2000) ‘Video surveillance research in retailing: ethical issues’, International Journal of Retail & Distribution Management, 28(11), pp. 470-480.
Klemke, L.W. (1992) The Sociology of Shoplifting: Boosters and Snitches Today. New York: Praeger. Langton, L. and Hollinger, R.C. (2005) ‘Correlates of Crime Losses in the Retail Industry’, Security Journal, 18(3), pp. 27-44.
Lawrence, G. (2004) ‘Designing out crime: the retail perspective’, International Journal of Retail & Distribution Management, 32(12), pp. 572-576. Lin, B., Hastings, D.A. and Martin, C. (1994) ‘Shoplifting in Retail Clothing Outlets: An Exploratory Research’, International Journal of Retail & Distribution Management, 22(7), pp. 24-29.
Liu, T. and Chen, C. (2011) ‘Please smile, the CCTV is running’, The Service Industries Journal, 31(7), pp. 1075-1092.
Loveday, K. and Gill, M. (2003) ‘The Impact of Monitored CCTV in a Retail Environment: What CCTV Operators Do and Why’, in Gill, M. (ed.) CCTV. Leicester: Perpetuity Press, pp. 109-126.
Mackay, D. (2006) ‘The Changing Nature of PublicSpace CCTV’, Security Journal, 19(2), pp. 128-142.
Mandeville, L. (1994) Customer Counting and Tracking Systems, RMDP Publications, London.
Mathieson, S. (2006) ‘John Lewis monitors moves on CCTV’, Network Security, 2006(3), pp. 1-2.
Mazerolle, L., Hurley, D. and Chamlin, M. (2002) ‘Social Behavior in Public Space: An Analysis of Behavioral Adaptations to CCTV’, Security Journal, 15(3), pp. 59-75.
McCahill, M. (2002) The Surveillance Web: The Rise of Visual Surveillance in an English City. Cullompton: Willan Publishing. McLuhan, R. (1999) ‘Impulse measures for POP creatvity’, Marketing, 6(June), pp. 31.
McNees, M., Egli, D., Marshall, R., Schnelle, J. and Risley, T. (1976) ‘Shoplifting Prevention: Providing Information Through Signs’, Journal of Applied Behavior Analysis, 9(4), pp. 399-405.
Murphy, D.J. (1986) Customers and Thieves. Aldershot: Gower Publishing Company Limited.
Nettle, D., Harper, Z., Kidson, A., Stone, R. and Penton-Voak, I.S. (2013) ‘The Watching Eyes Effect in the Dictator Game: It’s not how much you give, it’s being seen to give something’, Evolution and Human Behavior, 34, pp. 35-40.
Nettle, D., Nott, K. and Bateson, M. (2012) ‘‘Cycle Thieves, We Are Watching You’: Impact of a Simple Signage Intervention against Bicycle Theft’, PLoS ONE, 7(12).
Newman, G. (1997) ‘Introduction: Towards a Theory of Situational Crime Prevention’, in Newman, G., Clarke, R.V. and Shoham, S.G. (eds.) Rational Choice and Situational Crime Prevention. Aldershot: Ashgate, pp. 1-24.
Newman, O. (1996) Creating Defensible Space: Crime Prevention Through Urban Design. Washington DC: Office of Policy Development and Research, US Department of Housing and Urban Development.
Norris, C., Moran, J. and Armstrong, G. (1998) Surveillance, closed circuit television, and social control. Aldershot: Ashgate.
Oda, R., Niwa, Y., Honma, A. and Hiraishi, K. (2011) ‘An eye-like painting enhances the expectation of a good reputation’, Evolution and Human Behavior, 32, pp. 166-171.
Palmer, W. & Richardson, C. (2009) Organized Retail Crime: Assessing the Risk and Developing Effective Strategies, ASIS Foundation, Alexandria, VA.
Pawson, R. and Tilley, N. (1997) Realistic Evaluation. London: Sage Publications.
Phillips, H.C. and Bradshaw, R.P. (1991) ‘Camera tracking: a new tool for market research and retail management’, Management Research News, 14(4/5), pp. 20-22.
Rafacz, S.D., Boyce, T.E. and Williams, W.L. (2011) ‘Examining the Effects of a Low-Cost Prompt to Reduce Retail Theft’, Journal of Organizational Behavior Management, 31, pp. 150-160.
Reid, A. and Andresen, M. (2012) ‘An evaluation of CCTV in a car park using police and insurance data ‘, Security Journal, 27(1), pp. 55-79.
Sacco, V.F. (1985) ‘Shoplifting Prevention: The Role of Communication-Based Intervention Strategy’, Canadian Journal of Criminology, 27(1), pp. 15-29.
Schlueter, G.R., O’Neal, F.C., Hickey, J. and Seiler, G.L. (1989) ‘Rational vs. Nonrational Shoplifting Types: The Implications for Loss Prevention Strategies’, International Journal of Offender Therapy and Comparative Criminology, 33(December), pp. 227-239.
Shapland, J. (1995) ‘Preventing Retail-Sector Crimes’, in Tonry, M. and Farrington, D.P. (eds.) Building a Safer Society: Strategic Approaches to Crime Prevention. Chicago: The University of Chicago Press, pp. 263-342.
Sherman, L., Gottfredson, D., Mackenzie, S., Eck, J.E., Reuter, P. & Bushway, S. (1998) Preventing Crime: What Works, What Doesn’t, What’s Promising, National Institute of Justice, Washington.
Sivarajasingam, V. and Shepherd, J.P. (1999) ‘Effect of closed circuit television on urban violence’, Journal of Accident & Emergency Medicine, 16(4), pp. 255-257.
Slora, K.B. (1989) ‘An Empirical Approach to Determining Employee Deviance Base Rates’, Journal of Business and Psychology, 4, pp. 199-219.
Snowdon, R. (1995) ‘Why JWT is now asking the obvious’, Marketing, 14(September), pp. 16.
Stedmon, A.W., Harris, S. and Wilson, J.R. (2011) ‘Simulated multiplexed CCTV: The effects of screen layout and task complexity on user performance and strategies’, Security Journal, 24(4), pp. 344-356.
Thurber, S. and Snow, M. (1980) ‘Signs May Prompt Antisocial Behavior’, The Journal of Social Psychology, 112, pp. 309-210.
Tilley, N. (1997) ‘Realism, Situational Rationality and Crime Prevention’, in Newman, G., Clarke, R.V. and Shoham, S.G. (eds.) Rational Choice and Situational Crime Prevention. Aldershot: Ashgate, pp. 95-114.
Tonglet, M. (1998) ‘Consumers’ Perceptions of Shoplifting and Shoplifting Behaviour’, in Gill, M. (ed.) Crime at Work: Increasing the Risk for Offenders. Basingstoke: Palgrave Macmillan, pp. 107-122.
Tonglet, M. (2000) ‘Consumer Misbehaviour: Consumers’ Perceptions of Shoplifting and Retail Security’, Security Journal, 13(4), pp. 19-33.
Walsh, D.P. (1978) Shoplifting: Controlling a Major Crime. London: The Macmillan Press Ltd. Wanke, K. (2002) ‘How EAS Source Tagging Rewrote Shrinkage History in the Music and Video Sector’, Loss Prevention Magazine, May/June, pp. 33-38, 54.
Weaver, F. and Carroll, J. (1985) ‘Crime Perceptions in a Natural Setting by Expert and Novice Shoplifters’, Social Psychology Quarterly, 48(4), pp. 349-359.
Welsh, B. and Farrington, D.P. (2006) ‘ClosedCircuit Television Surveillance’, in Welsh, B. and Farrington, D.P. (eds.) Preventing Crime: What Works for Children, Offenders, Victims, and Places. Dordrecht: Springer, pp. 193-208.
Wilson, D. (2005) ‘Behind the Cameras: Monitoring and Open-street CCTV Surveillance in Australia’, Security Journal, 18(1), pp. 43- 54.
Wortley, R. (1997) ‘Reconsidering the Role of Opportunity in Situational Crime Prevention’, in Newman, G., Clarke, R.V. and Shoham, S.G. (eds.) Rational Choice and Situational Crime Prevention. Aldershot: Ashgate, pp. 65-82.
Zurawski, N. (2009) ‘‘It is all about perceptions’: Closed-circuit television, feelings of safety and perceptions of space – What the people say’, Security Journal, 23(4), pp. 259-275.
Endnotes
- Baumer, T.L. and Rosenbaum, D.P. (1984) Combatting Retail Theft: Programs and Strategies. Stoneham: Butterworth Publishers; Beck, A. (2009) New Loss Prevention: Redefining Shrinkage Management. Basingstoke: Palgrave MacMillan; Curtis, B. (1983) Retail Security: Controlling Loss for Profit. Boston: Butterworths; Johns, T. and Scicchitano, M. (2006) ‘Research by Retailers: Understanding Loss and the Effectiveness of Loss Prevention Strategies’, Security Journal, 19(4), pp. 216-227.
- Butler, G. (1994) ‘Shoplifters Views on Security: Lessons for Crime Prevention’, in Gill, M. (ed.) Crime at Work: Studies in Security and Crime Prevention. Leicester: Perpetuity Press, pp. 56-72; Caime, G. and Ghone, G. (1996) S(h) elf Help Guide: The Smart Lifters Handbook. Toronto: TriX Publishing; Clinard, M. and Meier, R. (1979) Sociology of Deviant Behavior. New York: Holt, Rinehart & Winston; Farrell, K. and Farrera, J. (1985) Shoplifting: The Anti-Shoplifting Guidebook. New York: Praeger.
- Capgemini & The Consumer Goods Forum 2015 Rethinking the Value Chain: New Realities in Collaborative Business, Capgemini and The Consumer Goods Forum.
- Clarke, R.V. (1980) ‘Situational Crime Prevention: Theory and Practice’, British Journal of Criminology, 20, pp. 136-147; Cornish, D.B. and Clarke, R.V. (1986) The Reasoning Criminal: Rational Choice Perspectives on Offending. New York: Springer-Verlag; Cusson, M. (1993) ‘Situational Deterrence: Fear During the Criminal Event’, in Clarke, R.V. (ed.) Crime Prevention Studies Volume 1. Monsey: Criminal Justice Press; Felson, M. (1986) ‘Linking Criminal Choices, Routine Activities, Informal Control, and Criminal Outcomes’, in Cornish, D.B. and Clarke, R.V. (eds.) The Reasoning Criminal. New York: Springer Verlag; Newman, G. (1997) ‘Introduction: Towards a Theory of Situational Crime Prevention’, in Newman, G., Clarke, R.V. and Shoham, S.G. (eds.) Rational Choice and Situational Crime Prevention. Aldershot: Ashgate, pp. 1-24; Tilley, N. (1997) ‘Realism, Situational Rationality and Crime Prevention’, in Newman, G., Clarke, R.V. and Shoham, S.G. (eds.) Rational Choice and Situational Crime Prevention. Aldershot: Ashgate, pp. 95-114; Wortley, R. (1997) ‘Reconsidering the Role of Opportunity in Situational Crime Prevention’, in Newman, G., Clarke, R.V. and Shoham, S.G. (eds.) Rational Choice and Situational Crime Prevention. Aldershot: Ashgate, pp. 65-82.
- See Cornish and Clarke (1986) op. cit.; Tilley (1997) op. cit.; Hayes, R. (1999) ‘Shop Theft: An Analysis of Shoplifter Perceptions and Situational Factors’, Security Journal, 12(2), pp. 7-18; Cardone, C. and Hayes, R. (2012) ‘Shoplifter Perceptions of Store Environments: An Analysis of how Physical Cues in the Retail Interior Shape Shoplifter Behavior’, Journal of Applied Security Research, 7(1), pp. 22-58.
- Hayes, R. (2012) ‘You Can Steal it, But You Can’t Use It: Moving Toward Benefit-Denial Technology’, LPPortal.Com, September-October, pp. 39-46; Davis, R. and Pease, K. (2000) ‘Crime, Technology and the Future’, Security Journal, 13(2), pp. 59-64; DiLonardo, R. and Clarke, R.V. (1996) ‘Reducing the Rewards of Shoplifting: An Evaluation of Ink Tags’, Security Journal, 71, pp. 11-14.
- Beck (2009) op. cit.
- Adapted from Cornish and Clarke (1986) op. cit. and Hayes (2012) op. cit.
- Klemke, L.W. (1992) The Sociology of Shoplifting: Boosters and Snitches Today. New York: Praeger; Cox, D., Cox, A.D. and Moschis, G.P. (1990) ‘When Consumer Behavior Goes Bad: An Investigation of Adolescent Shoplifting’, Journal of Consumer Research, 17(September), pp. 149-159. (Klemke, 1992, Cox, Cox and Moschis, 1990).
- Bamfield, J. (2012) Shopping and crime. Basingstoke: Palgrave Macmillan; Cameron, M.O. (1964) The Booster and the Snitch. New York: Free Press of Glencoe, Collier Macmillan; CarmelGilfilen, C. (2011) ‘Advancing Retail Security Design: Uncovering Shoplifter Perceptions of the Physical Environment’, Journal of Interior Design, 36(2), pp. 21-38; Clarke, R.V. & Petrossian, G. 2013 Shoplifting, Center for Problem-Oriented Policing, Washington; Gibbens, T.C.N. and Prince, J. (1962) Shoplifting. London: The Institute for the Study and Treatment of Delinquency; Gill, M. 2007a Shop Thieves Around the World, Perpetuity Research and Consulting International, Leicester; Hayes, R. and Cardone, C. (2006) ‘Shoptheft’, in Gill, M. (ed.) The Handbook of Security. Basingstoke: Palgrave Macmillan, pp. 302-327; Klemke (1992) op. cit.; Murphy, D.J. (1986) Customers and Thieves. Aldershot: Gower Publishing Company Limited’; Walsh, D.P. (1978) Shoplifting: Controlling a Major Crime. London: The Macmillan Press Ltd; Weaver, F. and Carroll, J. (1985) ‘Crime Perceptions in a Natural Setting by Expert and Novice Shoplifters’, Social Psychology Quarterly, 48(4), pp. 349-359.
- Beck (2009) op. cit.
- Hollinger, R.C. and Adams, A. (2008) 2007 National Retail Security Survey: Final Report. Gainsville, FL: University of Florida.
- Carmel-Glifilen (2011) op. cit.; Weaver and Carroll (1985) op. cit.
- See Gill (2007) op. cit.
- Palmer, W. & Richardson, C. (2009) Organized Retail Crime: Assessing the Risk and Developing Effective Strategies, ASIS Foundation, Alexandria, VA.
- See Butler (1994) op. cit.; Gill (2007a) op. cit.; Hayes, R. (2008) Lessons Learned: Shoplifter Interview Results, Loss Prevention Research Council, Florida.
- Ekblom, P. (1997) ‘Gearing up against crime: A dynamic framework to help designers keep up with the adaptive criminal in a changing world’, International Journal of Risk, Security and Crime Prevention, 2(4), pp. 249-265.
- Beck, A. and Willis, A. (1995) Crime and Security: Managing the Risk to Safe Shopping. Leicester: Perpetuity Press; Beck, A. and Willis, A. (1998) ‘Sales and Security: Striking the Balance’, in Gill, M. (ed.) Crime at Work: Increasing the Risk for Offenders. Basingstoke: Palgrave Macmillan, pp. 95-106; Carmel-Glifilen (2011) op. cit.; Weaver and Carroll (1985) op. it.
- Butler (1994) op. cit.; Hayes (2008) op. cit.
- Baumer and Rosenbaum (1984) op. cit.; Decker, S. (2003) ‘Advertising Against Crime: The Potential Impact of Publicity in Crime Prevention’, Criminology & Public Policy, 2(3), pp. 525-530.
- Shapland, J. (1995) ‘Preventing Retail-Sector Crimes’, in Tonry, M. and Farrington, D.P. (eds.) Building a Safer Society: Strategic Approaches to Crime Prevention. Chicago: The University of Chicago Press, pp. 263-342.
- Baumer and Rosenbaum (1984) op. cit. (Baumer and Rosenbaum, 1984).
- Beck (2009), op. cit.
- Beck and Willis (1998) op. cit.; Shapland (1995) op. cit.
- Sherman, L., Gottfredson, D., Mackenzie, S., Eck, J.E., Reuter, P. & Bushway, S. (1998) Preventing Crime: What Works, What Doesn’t, What’s Promising, National Institute of Justice, Washington; Farrington, D.P., Gottfredson, D., Sherman, L. and Welsh, B. (2002) ‘The Maryland Scientific Methods Scale’, in Sherman, L., Farrington, D.P., Welsh, B. and Mackay, D. (eds.) Evidence-Based Crime Prevention. 1st edn. London: Routledge, pp. 13-21.
- Pawson, R. and Tilley, N. (1997) Realistic Evaluation. London: Sage Publications; Hope, T. (2005) ‘Pretend It Doesn’t Work: The ‘AntiSocial’ Bias In The Maryland Scientific Methods Scale’, European Journal on Criminal Policy and Research, 11(3), pp. 275-296. (Pawson and Tilley, 1997).
- Farrington, D.P. (2003) ‘Methodological Quality Standards for Evaluation Research’, The Annals of the American Academy of Political and Social Science, 587, pp. 49-67. (Farrington, 2003)
- Sherman, L. et al (1998) op. cit. p.4.
- It is worth noting that IS typically have good internal validity (how well the research was conducted) but are often weak on external validity (applicability beyond the experimental group involved in the research).
- Farrington, D.P. and Painter, K. (2003) ‘How to Evaluate the Impact of CCTV on Crime’, in Gill, M. (ed.) CCTV. Leicester: Perpetuity Press, pp. 67-79.
- Beck (2009) op. cit.
- Beck and Willis (1998) op. cit.
- DiLonardo, R. (2014a) ‘EAS Source Tagging: 20- plus Years of Innovation, Part 1’, Loss Prevention Magazine, January-February, pp. 15-20, 22, 24; DiLonardo, R. (2014b) ‘EAS Source Tagging: 20- plus Years of Innovation, Part 2’, Loss Prevention Magazine, March-April, pp. 39-46, 48.
- DiLonardo (2014a), op. cit., p15.
- The term ‘taggant’ is used to describe any form of device that is attached to an object that enables a range of information types about that object to be identified. The simplest and most widely used form of taggant is the barcode, which enables details about the product to be shared, typically via infra red scanners or optical reading devices, which can then be associated with other data such as its current price. In terms of loss prevention, then the taggant is typically used to identify whether an item has been paid for or not, normally via the taggant being deactivated or removed from the product when purchased.
- Bickman, L., Rosenbaum, D.P., Baumer, T.L., Kudel, M., Christenholz, C., Knight, S. & Perkowitz, W. (1979) National Evaluation Program: Phase I Assessment of Shoplifting and Employee Theft Programs - Final Report: Programs and Strategies, Westinghouse Evaluation Institute, Evanston; Bauman and Rosenbaum (1984) op. cit. (Bickman et al, 1979, Baumer and Rosenbaum, 1984).
- Bamfield, J. (1994) ‘Article Surveillance: Management Learning in Curbing Theft’, in Gill, M. (ed.) Crime at Work: Studies in Security and Crime Prevention. Leicester: Perpetuity Press, pp. 156-174.
- DiLonardo and Clarke (1996) op. cit.; DiLonardo, R. (1997) ‘The Economic Benefit of Electronic Article Surveillance’, in Clarke, R.V. (ed.) Situational Crime Prevention: Successful Case Studies. New York: Harrow and Heston, pp. 122-131.
- Wanke, K. (2002) ‘How EAS Source Tagging Rewrote Shrinkage History in the Music and Video Sector’, Loss Prevention Magazine, May/ June, pp. 33-38, 54.
- Hayes, R. and Blackwood, R. (2006) ‘Evaluating the Effects of EAS on Product Sales and Loss: Results of a Large-Scale Field Experiment’, Security Journal, 19(4), pp. 262-276.
- Beck, A. and Palmer, W. (2011) ‘The Importance of Visual Situational Cues and Difficulty of Removal in Creating Deterrence: The Limitations of Electronic Article Surveillance Source Tagging in the Retail Environment’, Journal of Applied Security Research, 6(1), pp. 110-123; Hayes, R., Johns, T., Scicchitano, M., Downs, D. and Pietrawska, B. (2011) ‘Evaluating the effects of protective keeper boxes on ‘hot product’ loss and sales: A randomized controlled trial’, Security Journal, 24(4), pp. 357-369; Hayes, R. and Downs, D. (2011) ‘Controlling retail theft with CCTV domes, CCTV public view monitors, and protective containers: A randomized controlled trial’, Security Journal, 24(3), pp. 237-250.
- Sherman, L. et al (1998) op. cit. (Sherman et al, 1998).
- Wanke (2002) op. cit.
- Farrington (2003) op. cit.
- Weaver and Carroll (1985) op. cit.; Gill, M., Bilby, C. and Turbin, V. (1999) ‘Retail Security: Understanding What Deters Shop Thieves’, Journal of Security Administration, 22(1), pp. 29-40; Gill (2007a) op. cit.; Gill, M. (2007b) Shoplifters on Shop Theft: Implications for Retailers, Perpetuity Research & Consultancy International, Leicester.
- Hayes, R. (1999) op. cit.
- Lasky, N.V., Fisher, B.S. and Jacques, S. (2015) ‘‘Thinking Thief’ in the Crime Prevention Arms Race: Lessons Learned From Shoplifters’, Security Journal, , pp. 1-21.
- Gill (2007a) op. cit.
- Beck, A. and Willis, A. (1994) An Evaluation of Security Hardware: The Customer Perspective, Centre for the Study of Public Order: Leicester. This study found that of 483 customers interviewed just 30% had noticed any form of security in the store.
- Weaver and Carroll (1985) op. cit.; CarmelGilfilen (2011) op. cit.
- Decker (2003) op. cit.
- Handford, M. (1994) ‘Electronic Tagging in Action: A Case Study in Retailing’, in Gill, M. (ed.) Crime at Work: Studies in Security and Crime Prevention. Leicester: Perpetuity Press, pp. 175-184; Hayes and Blackwood (2006) op. cit.
- Beck and Willis (1994) op. cit.
- Butler (1994) op. cit.; Guffey, H., Harris, J. and Laumer, J. (1979) ‘Shopper Attitudes Toward Shoplifting and Shoplifting Devices’, Journal of Retailing, 55(Fall), pp. 75-89; Kallis, M.J. and Vanier, D.J. (1985) ‘Consumer Shoplifting: Orientations and Deterrents’, Journal of Criminal Justice, 13(5), pp. 459-473; Schlueter, G.R., O’Neal, F.C., Hickey, J. and Seiler, G.L. (1989) ‘Rational vs. Nonrational Shoplifting Types: The Implications for Loss Prevention Strategies’, International Journal of Offender Therapy and Comparative Criminology, 33(December), pp. 227-239; Slora, K.B. (1989) ‘An Empirical Approach to Determining Employee Deviance Base Rates’, Journal of Business and Psychology, 4, pp. 199-219; Weaver and Carroll (1985) op. cit.
- Norris, C., Moran, J. and Armstrong, G. (1998) Surveillance, closed circuit television, and social control. Aldershot: Ashgate.
- Norris, C., Moran, J. and Armstrong, G. (1998) Surveillance, closed circuit television, and social control. Aldershot: Ashgate; Farrington and Painter (2003) op. cit.; McCahill, M. (2002) The Surveillance Web: The Rise of Visual Surveillance in an English City. Cullompton: Willan Publishing; Welsh, B. and Farrington, D.P. (2006) ‘ClosedCircuit Television Surveillance’, in Welsh, B. and Farrington, D.P. (eds.) Preventing Crime: What Works for Children, Offenders, Victims, and Places. Dordrecht: Springer, pp. 193-208.
- Ballantyne, H., Medway, D. and Jones, P. (2001) ‘CCTV and Town Centre Regeneration’, Town and Country Planning; Beck, A. 2008 Preventing Retail Shrinkage: Measuring the ‘Value’ of CCTV, EAS and Data Mining Tools, ECR Europe, Brussels; Gill, M. & Spriggs, A. (2005) Assessing the Impact of CCTV, Home Office, London.
- Harris, C., Jones, P., Hillier, D. and Turner, D. (1998) ‘CCTV Surveillance Systems in Town and City Centre Management’, Property Management, 16(3), pp. 1-6; Hesse, L. (2002) ‘The Transition from Video Motion Detection to Intelligent Scene Discrimination and Target Tracking in Automated Video Surveillance Systems’, Security Journal, 15(2), pp. 69-78.
- See for instance: Kirkup, M. (1999) ‘Electronic footfall monitoring: experiences among UK clothing multiples’, International Journal of Retail and Distribution Management, 27(4), pp. 166- 73; Kirkup, M. and Carrigan, M. (2000) ‘Video surveillance research in retailing: ethical issues’, International Journal of Retail & Distribution Management, 28(11), pp. 470-480; Liu, T. and Chen, C. (2011) ‘Please smile, the CCTV is running’, The Service Industries Journal, 31(7), pp. 1075-1092; Mackay, D. (2006) ‘The Changing Nature of Public-Space CCTV’, Security Journal, 19(2), pp. 128-142.
- McCahill (2002) op. cit.
- Gill, M. and Turbin, V. (1998) ‘CCTV and Shop Theft: Towards a Realistic Evaluation’, in Norris, C., Moran, J. and Armstrong, G. (eds.) Surveillance, Closed Circuit Television and Social Control. Aldershot: Ashgate, pp. 189-204.
- Beck, A. and Willis, A. (1999) ‘Context-Specific Measures of CCTV Effectiveness in the Retail Sector’, in Painter, K. and Tilley, N. (eds.) Surveillance of Public Space: CCTV, Street Lighting and Crime Prevention. New York: Criminal Justice Press, pp. 251-269.
- Hayes, R. and Downs, D. (2011) op. cit.
- Baumer and Rosenbaum (1984) op. cit.; Butler (1994) op. cit.; Cardone (2006) op. cit.; Clarke and Petrossian (2013) op. cit.; Carmel-Gilfilen (2011) op. cit.; Welsh and Farrington (2006) op. cit.
- Gill (2007a, 2007b) op. cit.; Hayes (1999) op. cit.
- Lasky et al (2015) op. cit.
- Beck, A. & Willis, A. 1992 An Evaluation of Store Security and Closed Circuit Television, University of Leicester, Centre for the Study of Public Order, Leicester; Kajalo, S. and Lindblom, A. (2010a) ‘How retail entrepreneurs perceive the link between surveillance, feeling of security, and competitiveness of the retail store? A structural model approach’, Journal of Retailing and Consumer Services, 17(4), pp. 300-305; Kajalo, S. and Lindblom, A. (2010b) ‘Surveillance investments in store environment and sense of security’, Facilities, 28(9/10), pp. 465-474; Kajalo, S. and Lindblom, A. (2011a) ‘An empirical analysis of retail entrepreneurs’ approaches to prevent shoplifting’, Security Journal, 24(4), pp. 269-282; Kajalo, S. and Lindblom, A. (2011b) ‘Effectiveness of formal and informal surveillance in reducing crime at grocery stores’, Journal of Small Business and Enterprise Development, 18(1), pp. 157-169.
- Gill and Spriggs (2005) op. cit.; Keval, H. and Sasse, M.A. (2008; 2010) ‘“Not the Usual Suspects”: A study of factors reducing the effectiveness of CCTV’, Security Journal, 23(2), pp. 134-154; Loveday, K. and Gill, M. (2003) ‘The Impact of Monitored CCTV in a Retail Environment: What CCTV Operators Do and Why’, in Gill, M. (ed.) CCTV. Leicester: Perpetuity Press, pp. 109-126; McCahill (2002) op. cit.; Stedmon, A.W., Harris, S. and Wilson, J.R. (2011) ‘Simulated multiplexed CCTV: The effects of screen layout and task complexity on user performance and strategies’, Security Journal, 24(4), pp. 344-356; Wilson, D. (2005) ‘Behind the Cameras: Monitoring and Open-street CCTV Surveillance in Australia’, Security Journal, 18(1), pp. 43- 54.
- Ballantyne et al (2001) op. cit.; Dodd, C.A., Clarke, I. and Kirkup, M. (1998) ‘Camera observations of customer behaviour in fashion retailing: methodological propositions’, International Journal of Retail & Distribution Management, 26(8), pp. 1-8; Gladwell, M. (1997) ‘See me, touch me’, The Independent Magazine, (February), pp. 9-12; Kirkup (1999) op. cit.; Kirkup and Carrigan (2000) op. cit.; Mackay, D. (2006) op. cit.; Mandeville, L. 1994 Customer Counting and Tracking Systems, RMDP Publications, London; Mathieson, S. (2006) ‘John Lewis monitors moves on CCTV’, Network Security, 2006(3), pp. 1-2; McLuhan, R. (1999) ‘Impulse measures for POP creativity’, Marketing, 6(June), pp. 31; Phillips, H.C. and Bradshaw, R.P. (1991) ‘Camera tracking: a new tool for market research and retail management’, Management Research News, 14(4/5), pp. 20-22; Snowdon, R. (1995) ‘Why JWT is now asking the obvious’, Marketing, 14(September), pp. 16; Zurawski, N. (2009) ‘‘It is all about perceptions’: Closed-circuit television, feelings of safety and perceptions of space – What the people say’, Security Journal, 23(4), pp. 259-275.
- Welsh and Farrington (2009) op. cit.
- Beck and Willis (1994, 1998) op. cit.; Harris et al (1998) op. cit.; Hesse (2002) op. cit.; Mazerolle, L., Hurley, D. and Chamlin, M. (2002) ‘Social Behavior in Public Space: An Analysis of Behavioral Adaptations to CCTV’, Security Journal, 15(3), pp. 59-75; Reid, A. and Andresen, M. (2012) ‘An evaluation of CCTV in a car park using police and insurance data’, Security Journal, 27(1), pp. 55-79; Sivarajasingam, V. and Shepherd, J.P. (1999) ‘Effect of closed circuit television on urban violence’, Journal of Accident & Emergency Medicine, 16(4), pp. 255-257;
- Johnson, S. and Bowers, K. (2003) ‘Opportunity is in the Eye of the Beholder: The Role of Publicity in Crime Prevention’, Criminology & Public Policy, 2(3), pp. 497-524.
- Decker (2003) op. cit.; Sacco, V.F. (1985) ‘Shoplifting Prevention: The Role of CommunicationBased Intervention Strategy’, Canadian Journal of Criminology, 27(1), pp. 15-29.
- Nettle, D., Nott, K. and Bateson, M. (2012) ‘‘Cycle Thieves, We Are Watching You’: Impact of a Simple Signage Intervention against Bicycle Theft’, PLoS ONE, 7(12); Nettle, D., Harper, Z., Kidson, A., Stone, R. and Penton-Voak, I.S. (2013) ‘The Watching Eyes Effect in the Dictator Game: It’s not how much you give, it’s being seen to give something’, Evolution and Human Behavior, 34, pp. 35-40; Oda, R., Niwa, Y., Honma, A. and Hiraishi, K. (2011) ‘An eye-like painting enhances the expectation of a good reputation’, Evolution and Human Behavior, 32, pp. 166-171.
- Hartmann, D.P., Gelfand, D.M., Page, B. and Walder, P. (1972) ‘Rates of Bystander Observation and Reporting of Contrived Shoplifting Incidents’, Criminology, 10(3), pp. 247-267. (Hartmann et al, 1972)
- McNees, M., Egli, D., Marshall, R., Schnelle, J. and Risley, T. (1976) ‘Shoplifting Prevention: Providing Information Through Signs’, Journal of Applied Behavior Analysis, 9(4), pp. 399-405. (McNees et al, 1976)
- Bickman, L. and Green, S.K. (1977) ‘Situational Cues and Crime Reporting: Do Signs Make a Difference?’, Journal of Applied Social Psychology, 7(1), pp. 1-18.
- Carter, N., Hansson, L., Holmberg, B. and Melin, L. (1979) ‘Shoplifting Reduction Through the Use of Specific Signs’, Journal of Organizational Behavior Management, 2, pp. 73-84. (Carter et al, 1979).
- Buckle et al (1992) op. cit. (Buckle et al, 1992)
- Thurber, S. and Snow, M. (1980) ‘Signs May Prompt Antisocial Behavior’, The Journal of Social Psychology, 112, pp. 309-210.
- Carter, N., Holmstrom, A., Simpanen, M. and Melin, L. (1988) ‘Theft Reduction in a Grocery Store Through Product Identification and Graphing of Losses for Employees’, Journal of Applied Behavior Analysis, 21(4), pp. 385-389.
- Carter, N. and Holmberg, B. (1992) ‘Theft Reduction in a Grocery Store Through Product Identification’, Journal of Organizational Behavior Management, 13(1), pp. 129-135.
- Rafacz, S.D., Boyce, T.E. and Williams, W.L. (2011) ‘Examining the Effects of a Low-Cost Prompt to Reduce Retail Theft’, Journal of Organizational Behavior Management, 31, pp. 150-160. (Rafacz, Boyce and Williams, 2011)
- Butler (1994) op. cit.
- Buckle et al (1992) op. cit.
- Farrington, D.P. (1999) ‘Measuring, Explaining and Preventing Shoplifting: A Review of British Research’, Security Journal, 12(1), pp. 9-27. (Farrington, 1999).
- Walsh (1978) op. cit. (Walsh, 1978)
- Carmel-Gilfilen (2011) op. cit.; Carmel-Gilfilen, C. (2013) ‘Bridging security and good design: Understanding perceptions of expert and novice shoplifters’, Security Journal, 26(1), pp. 80-105. (Carmel-Gilfilen, 2011, Carmel-Gilfilen, 2013).
- Butler (1994) op. cit. (Butler, 1994).
- Gill (2007a) op. cit.
- Hayes (1999) op. cit.; Hayes, R. (ed.) (2006) Shoplifting Mach 3: Offender Interviews Research. Presentation Slides. Unpublished. (Hayes, 1999, Hayes, 2006).
- Guffey et al (1979) op. cit.
- Kallis and Vanier (1985) op. cit. (Kallis and Vanier, 1985).
- Schlueter et al (1989) op. cit.
- Kajalo and Lindblom (2010a, 2010b, 2011a, 2011b) op. cit. (Kajalo and Lindblom, 2010, Kajalo and Lindblom, 2011, Kajalo and Lindblom, 2010, Kajalo and Lindblom, 2011).
- Tonglet, M. (2000) ‘Consumer Misbehaviour: Consumers’ Perceptions of Shoplifting and Retail Security’, Security Journal, 13(4), pp. 19-33; Tonglet, M. (1998) ‘Consumers’ Perceptions of Shoplifting and Shoplifting Behaviour’, in Gill, M. (ed.) Crime at Work: Increasing the Risk for Offenders. Basingstoke: Palgrave Macmillan, pp. 107-122. (Tonglet, 1998, Tonglet, 2000).
- Lin, B., Hastings, D.A. and Martin, C. (1994) ‘Shoplifting in Retail Clothing Outlets: An Exploratory Research’, International Journal of Retail & Distribution Management, 22(7), pp. 24- 29. (Lin, Hastings and Martin, 1994).
- Langton, L. and Hollinger, R.C. (2005) ‘Correlates of Crime Losses in the Retail Industry’, Security Journal, 18(3), pp. 27-44.
- Howell, S.D. and Proudlove, N.C. (2007) ‘A statistical investigation of inventory shrinkage in a large retail chain’, The International Review of Retail, Distribution and Consumer Research, 17(2), pp. 101-120. (Howell and Proudlove, 2007).
- Capgemini & The Consumer Goods Forum (2015) op. cit.
- Jeffery, C.R. (1977) Crime Prevention Through Environmental Design. 2nd Edition edn. Beverly Hills: Sage; Newman, O. (1996) Creating Defensible Space: Crime Prevention Through Urban Design. Washington DC: Office of Policy Development and Research, US Department of Housing and Urban Development. (Jeffery, 1977, Newman, 1996).
- Demkin, J. (ed.) (2004) Security Planning and Design: A Guide for Architects and Building Design Professionals Hoboken, NJ: John Wiley & Sons, quoted in Carmel Gilfilen (2013) op. cit.
- Buckle et al (1994) op. cit. (Buckle et al, 1992).
- Farrington (1999) op. cit. (Farrington, 1999).
- Carmel-Gilfilen (2011, 2013) op. cit.
- Carmel Gilfilen (2013) op. cit. p. 95.
- Gill (2007a) op. cit.
- Cardone, C. (2006) Opportunity makes the thief: An analysis of the physical cues that influence shoplifter perceptions of the retail interior and the decision to steal. MA. University of Florida. Available at: http://ufdc.ufl.edu/ UFE0015826/00001/ (Accessed: 20/3/16), pp. 22-58; Cardone and Hayes (2012) op. cit.
- Crowe, T. (2000) Crime Prevention Through Environmental Design. 2nd edn. Boston: Butterworth-Heinemann.
- Lawrence, G. (2004) ‘Designing out crime: the retail perspective’, International Journal of Retail & Distribution Management, 32(12), pp. 572-576.
- Kajalo and Lindblom (2010a, 2010b, 2011a, 2011b) op. cit.
- Abelson, E. (1989) When Ladies Go A Thieving. New York: Oxford University Press.
- Clarke and Petrossian (2013) op. cit.
- Ekblom, P. (1986) The Prevention of Shop Theft: An Approach Through Crime Analysis. Crime Prevention Unit Paper No. 5, London: Home Office; Gill (2007a); Hayes and Cardone (206) op. cit.
- Lasky et al (2015) op. cit. in interviews with shoplifters found that they either ignored them or tried to use them to their advantage to keep an eye on the location of store staff.
- Clarke and Petrossian (2013) op. cit.
- Carmel-Gilfilen (2013) op. cit.
- Hayes, R., Downs, D. and Blackwood, R. (2011) ‘Anti-theft Procedures and Fixtures: A Randomized Controlled Trial of Two Situational Crime Prevention Measures’, Journal of Experimental Criminology, 8(1), pp. 1-15.
- Hayes and Downs (2011) op. cit.
- For instance the work of Carmel-Glifilen (2011) op. cit., which replicated the study of Weaver and Carroll (1985) op. cit. found very similar results whereas the replication study by Rafacz et al (2011) op. cit. of the Carter et al (1979) op. cit. study did not.
- The Hawthorne Effect derives its name from a productivity study undertaken in the 1920s at the Hawthorne Plant of the Western Electric Company in Cicero, Illinois. If found that workers increased their productivity when they were studied, but it declined when the study finished. The results implied that participants in research studies may change their behaviour simply because of the attention they receive, regardless of any experimental manipulation. Within a retail context, where for instance a study might be focused on the impact an intervention has on external theft, it can be very challenging to control for the effect of the study taking place on internal thieves who may suspend their miscreant behavior while the research underway.
- See Beck (2009) op. cit. for a discussion on the problems associated with the term ‘shrinkage’ and how retailers vary in the way in which it used to capture retail losses.
- See Tilley and Pawson (1997) op. cit.
- See Beck, A. and Hopkins, M. (forthcoming) Scan and rob! Convenience shopping, crime opportunity and corporate social responsibility in a mobile world, Security Journal.
- For more information: http://ecr-shrink-group. com; http://www.rila.org/Pages/default.aspx.
- Beck and Palmer (2011) op. cit.
- The author is aware of some interesting unpublished research undertaken by Checkpoint Systems on different symbols and stickers, and product designs incorporating them, and the degree to which they are noticed by customers and thieves.
- See for instance Barua, A., Mani, D. & Whinston, A.B. n.d. Assessing the Financial Impacts of RFID Technologies on the Retail and Healthcare Sectors, Center for Research in Electronic Commerce, Austin; Beck, A. and Hopkins, M. (2015) Developments in Retail Mobile Scanning Technologies: Understanding the Potential Impact on Shrinkage & Loss Prevention, Leicester: University of Leicester; Dubash, J. (2016) ‘Marketing and the Internet of Things: Are You Ready?’, The Marketing Journal.
- Rafacz et al (2011) op. cit.
- Hayes and Downs (2011) op. cit.
- Beck, A. (2011) ‘Self-scan checkouts and retail loss: Understanding the risk and minimising the threat’, Security Journal, 24(3), pp. 199-217.
- See for instance: Ariely, D. (2012) The (Honest) Truth About Dishonesty. New York: Harper Collins. 133. Beck and Hopkins (2015 and forthcoming) op. cit. 134. Capgemini & The Consumer Good Forum (2015) op. cit.
Main office
ECR Community a.s.b.l
Upcoming Meetings
Join Our Mailing List
Subscribe© 2023 ECR Retails Loss. All Rights Reserved|Privacy Policy